OpenWrt - Network Configuration

Firewall, port forwarding, etc.? What and how should this get configured to make our services available?
This article describes exemplary how to make the necessary adjustments to the firewall
All articles of the OpenWrt series
OpenWrt - Overview
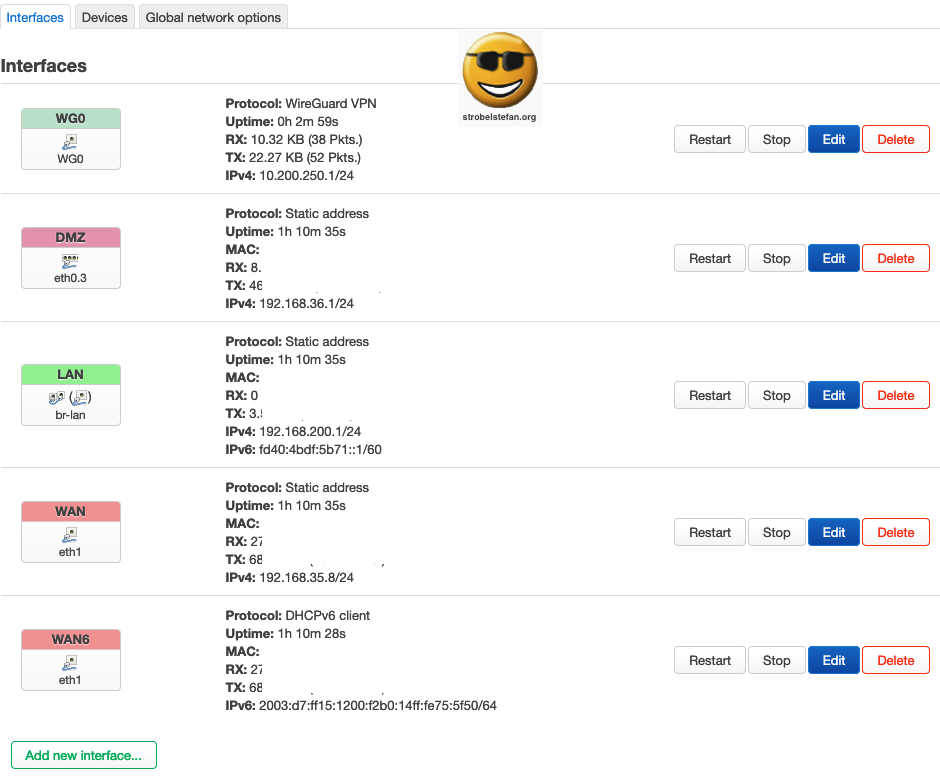
Interfaces Configuration
OpenWrt universally distinguishes between two types of software network interfaces:
- Physical devices
- Virtual Network Interfaces (see ➡️ Switches)
Links:
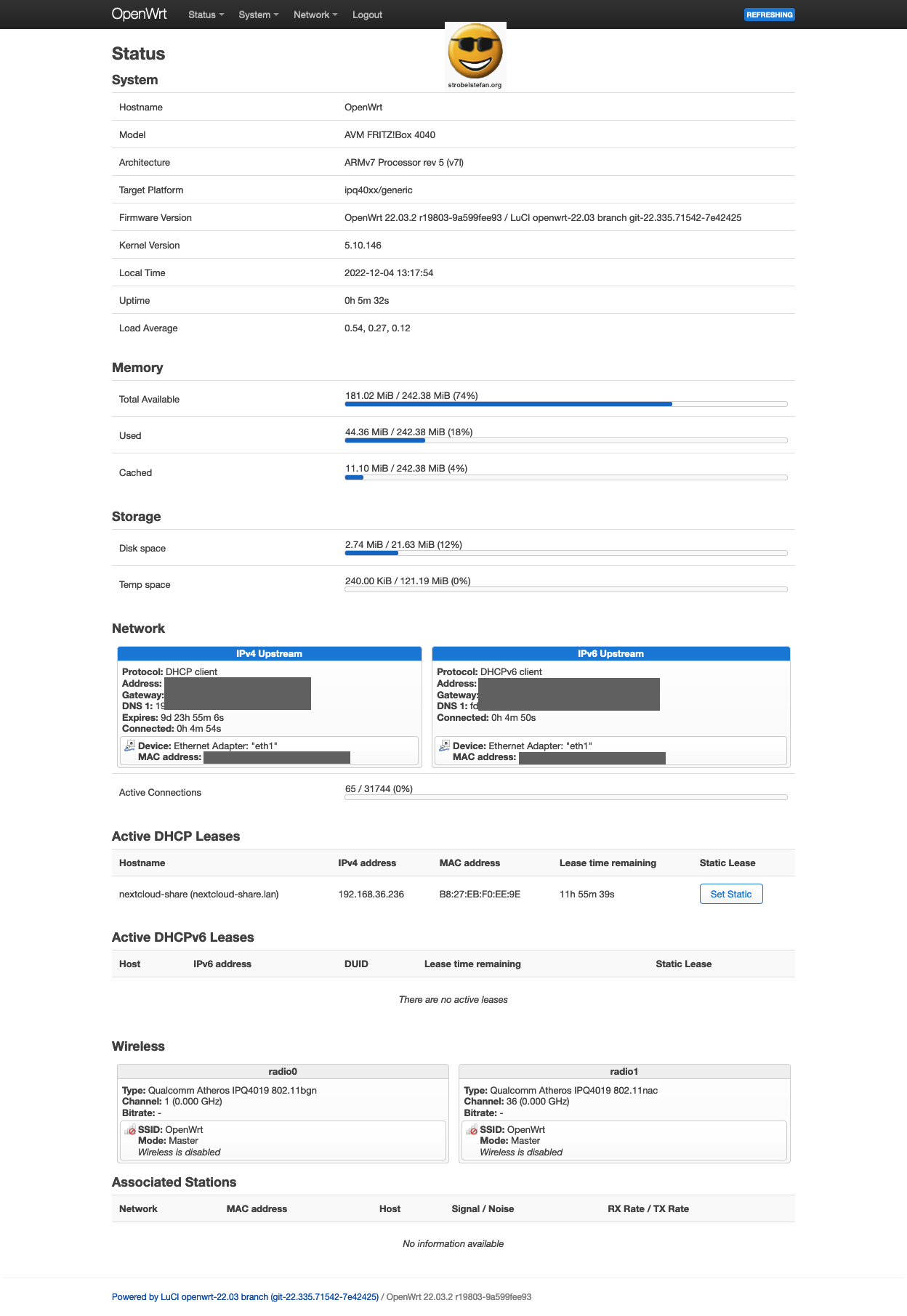
The OpenWrt setup uses the interfaces as shown in the screenshot.
WAN Interface
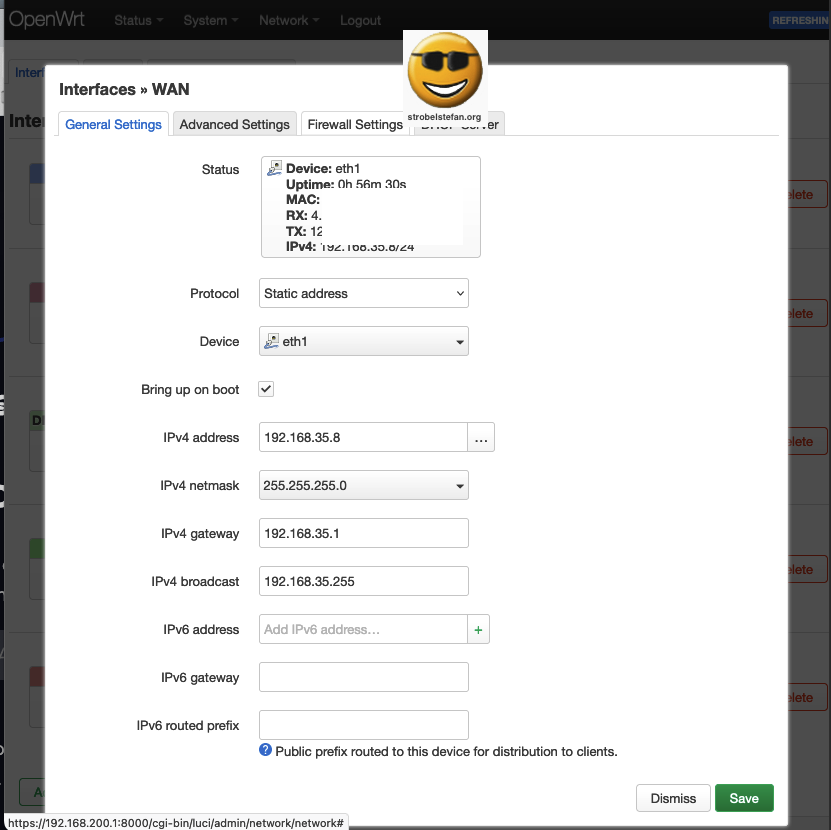
The WAN interface is the connection between the OpenWrt device (= AVM FRITZ!Box 4040) and the network router (= AVM FRITZ!Box 7490)
The IP address of the OpenWrt device is configured in the router's network settings to 192.168.xxx.xxx.
General Settings
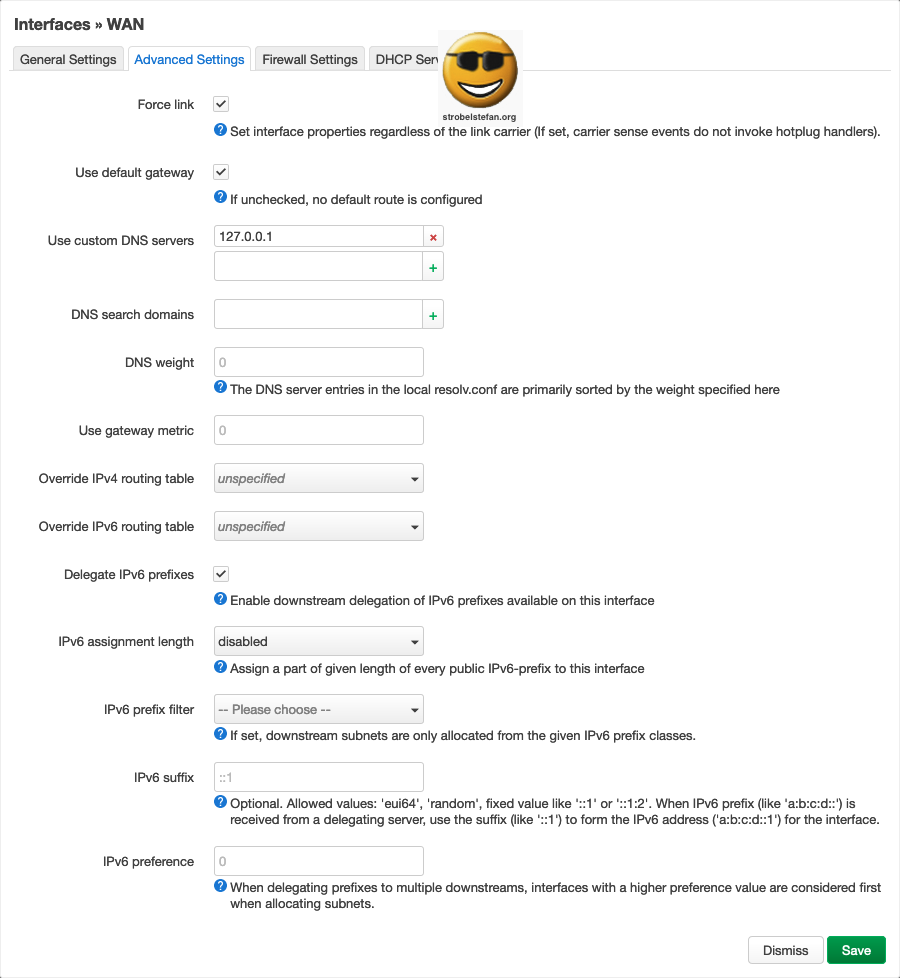
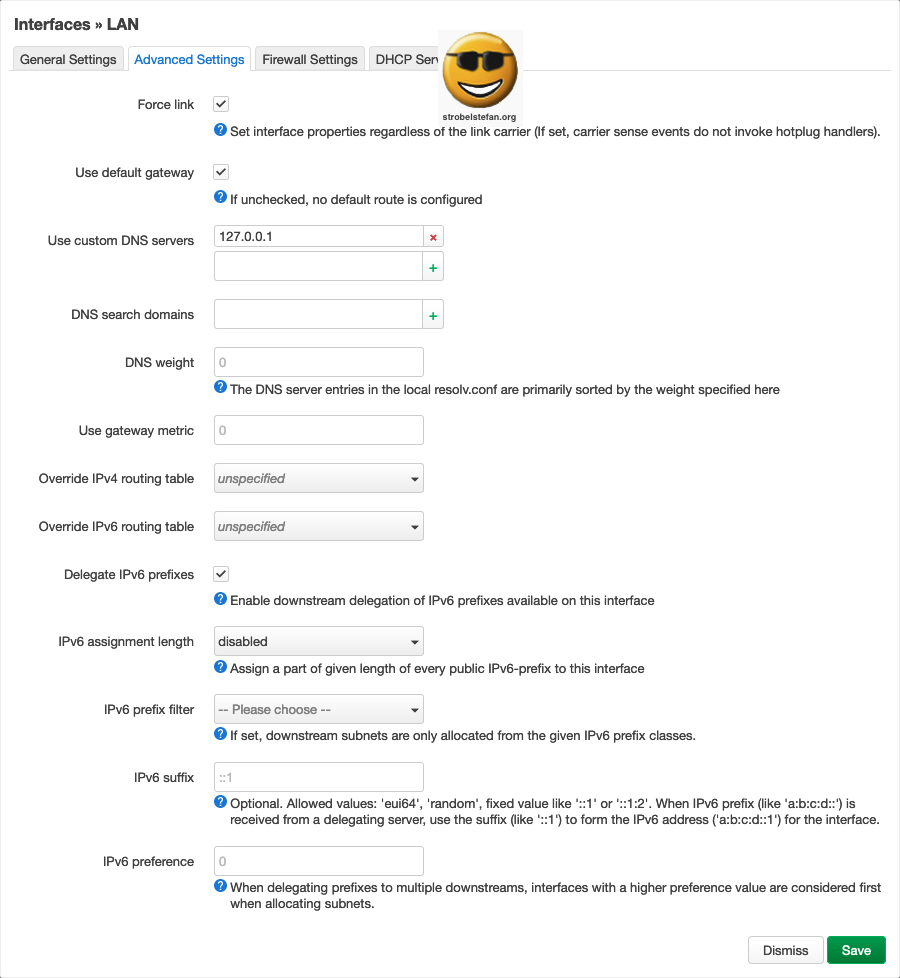
The option Masquerading must be checked otherwise the WireGuard interface is not able to use the networks DNS server.
The DNS server is redirected to the local DNS server 127.0.0.1.
The DNS documentation is explained in detail in the manual ➡️ OpenWrt - Stubby & DNSMASQ
Advanced Settings
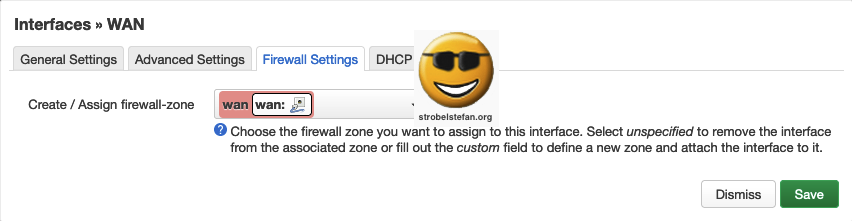
Firewall Settings
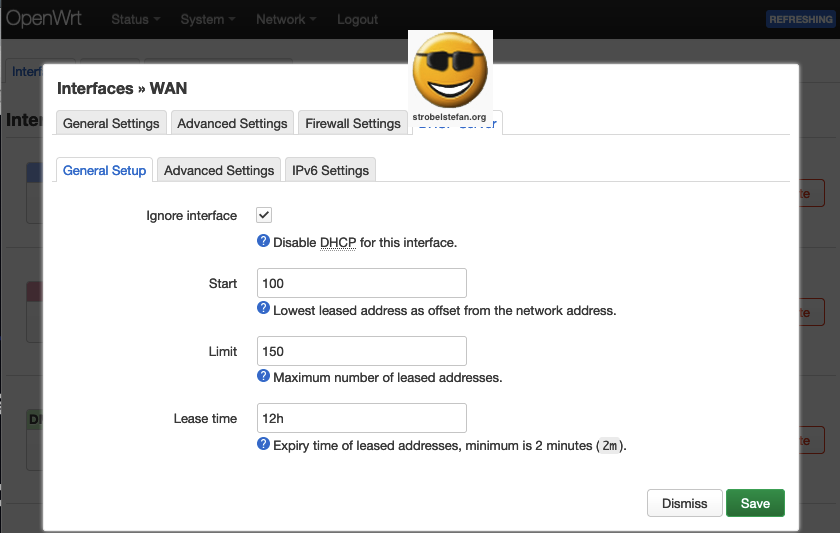
DHCP Server - General Settings
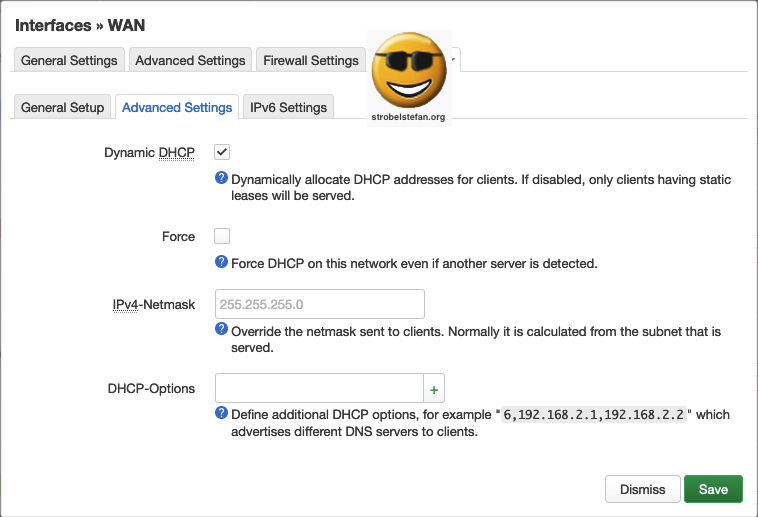
DHCP Server - Advanced Settings
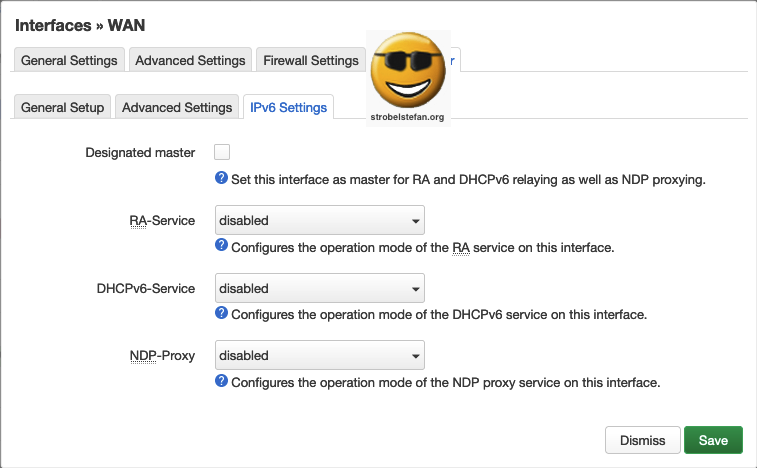
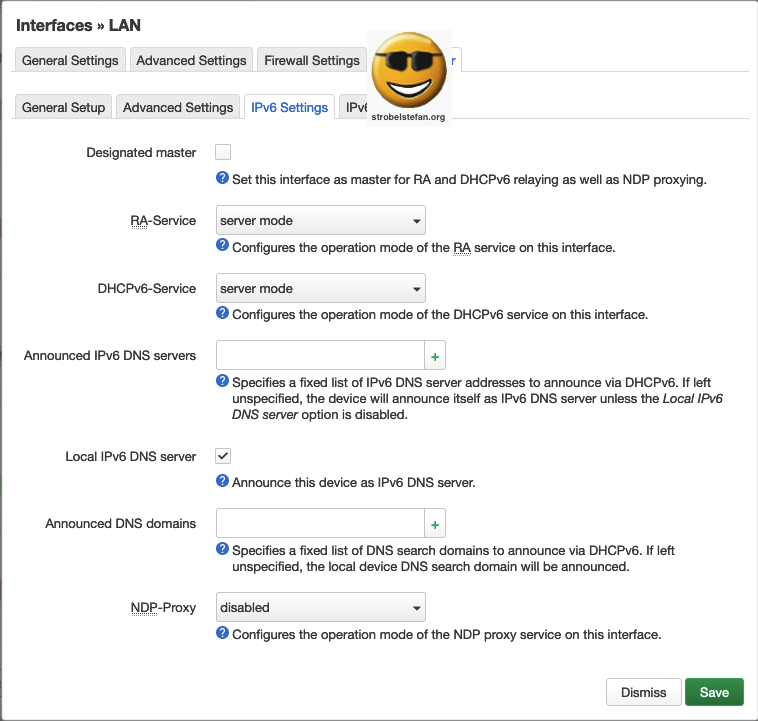
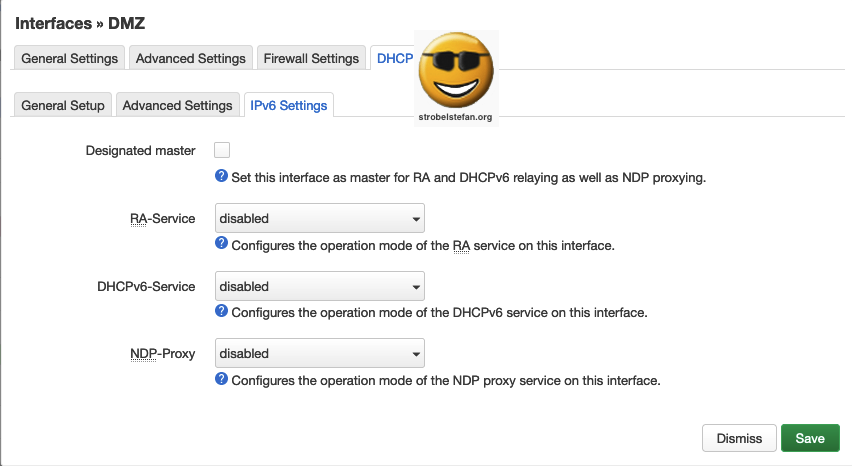
IPv6 is not in use in the network.
DHCP Server - IPv6 Settings
LAN Interface
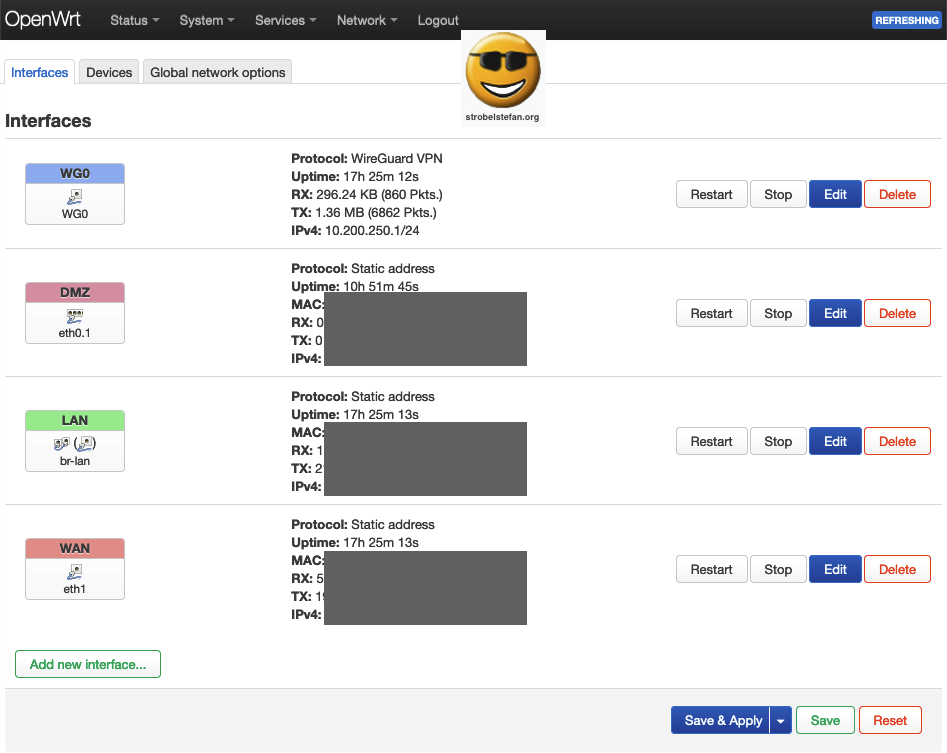
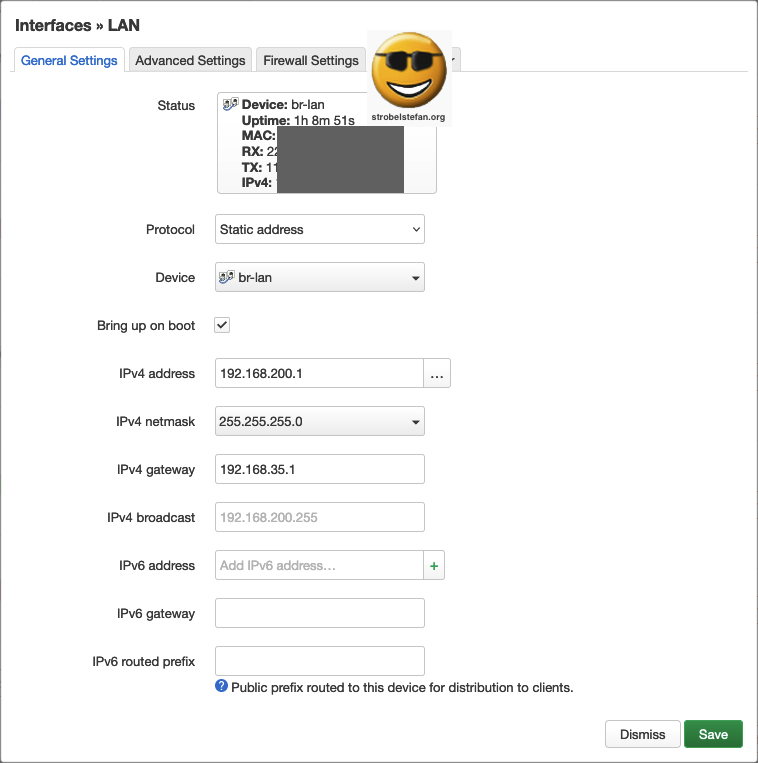
The IP address of the OpenWrt device is set to a static address which is configured in Interfaces - LAN - General Settings
IP address: 192.168.200.1
The IP range is 192.168.200.1 - 192.168.200.255
The network interface lan is a bridge from one network segment to the other.
The IPv4 gateway is the IP address of the router. (please refer to ➡️ AMV Router Configuration)
General Settings
Advanced Settings
Firewall Settings
DHCP Server - General Setup
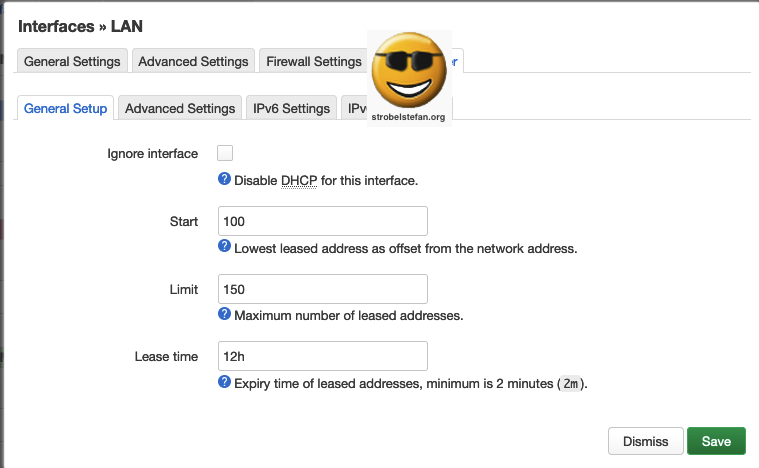
DHCP Server - Advanced Setup
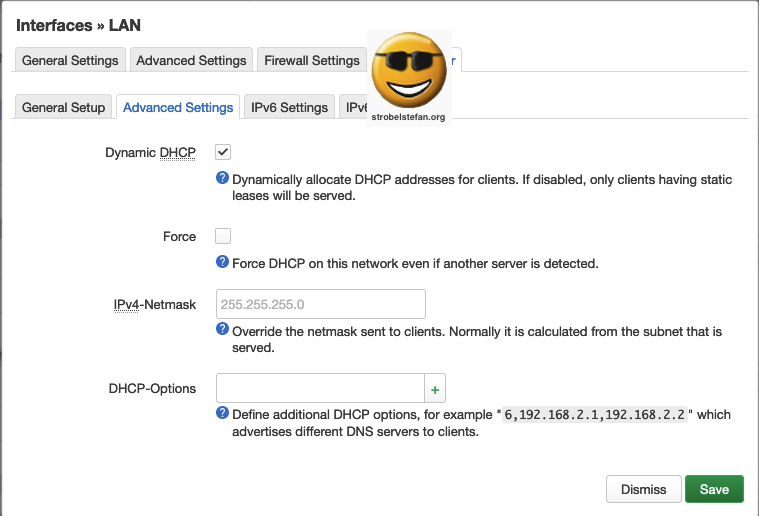
DHCP Server - IPv6 Settings
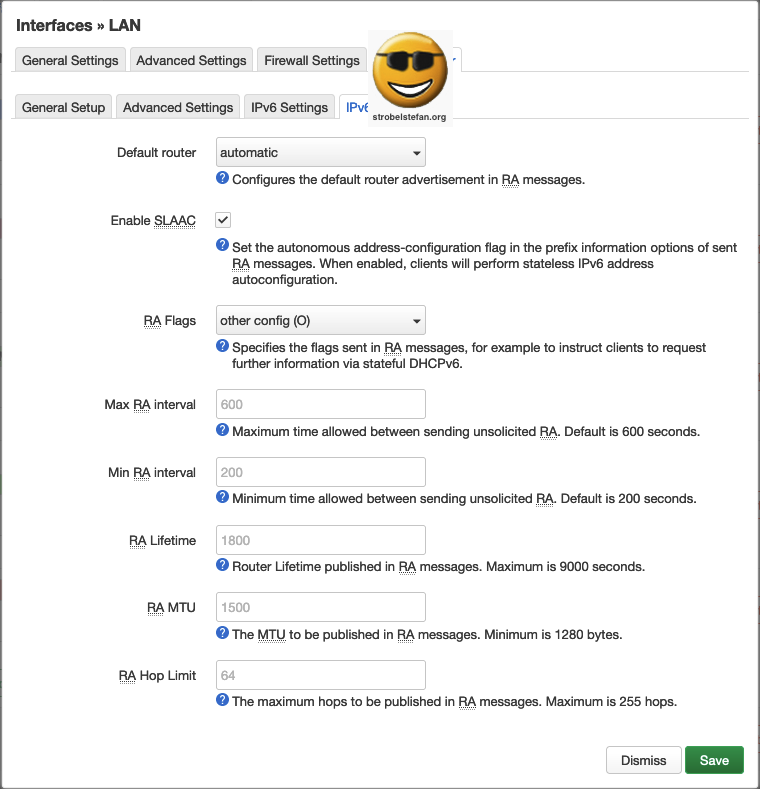
DHCP Server - IPv6 RA Settings
Services, Tools and Apps
If you need to access special services, tools and apps from your lan you have to open the specific port in your firewall.
In the table below some are listed.
| Name | Port | TCP or UDP | Link |
|---|---|---|---|
| http | 80 | TCP | de.wikipedia.org |
| https | 443 | TCP | de.wikipedia.org |
| SSH | 22 | TCP | SSH Port, de.wikipedia.org |
| borgbackup | 23 | TCP | Hetzner Storage Box mit BorgBackup nutzen, Hetzner Hilfe |
| DNS | 53 | TCP | de.wikipedia.org |
| DNS | 853 | TCP | de.wikipedia.org |
| NTP | 123 | TCP / UDP | de.wikipedia.org |
| smtp | 465 | TCP | Nextcloud Installation, de.wikipedia.org, Strato Hilfe, Google Developer, web.de |
| imap | 993 | TCP | de.wikipedia.org, Strato Hilfe, Google Developer, web.de |
| Syncthing | 8384 | TCP | docs.syncthing.net |
| mosh | 60000 - 61000 | UDP | mosh.org, de.wikipedia.org |
| CalDav | TCP | e.g. Synology, mailbox.org, posteo.de | |
| CardDav | TCP | e.g. Synology, mailbox.org, posteo.de |
DMZ Interface
A DMZ is only recommended when a server shall be accessible from the internet.
In this example Nextcloud server is set into DMZ and made accessible from the internet.
The DMZ uses the VLAN configuration. The Device must be set to the respective VLAN.
- ➡️ Switches
General Settings
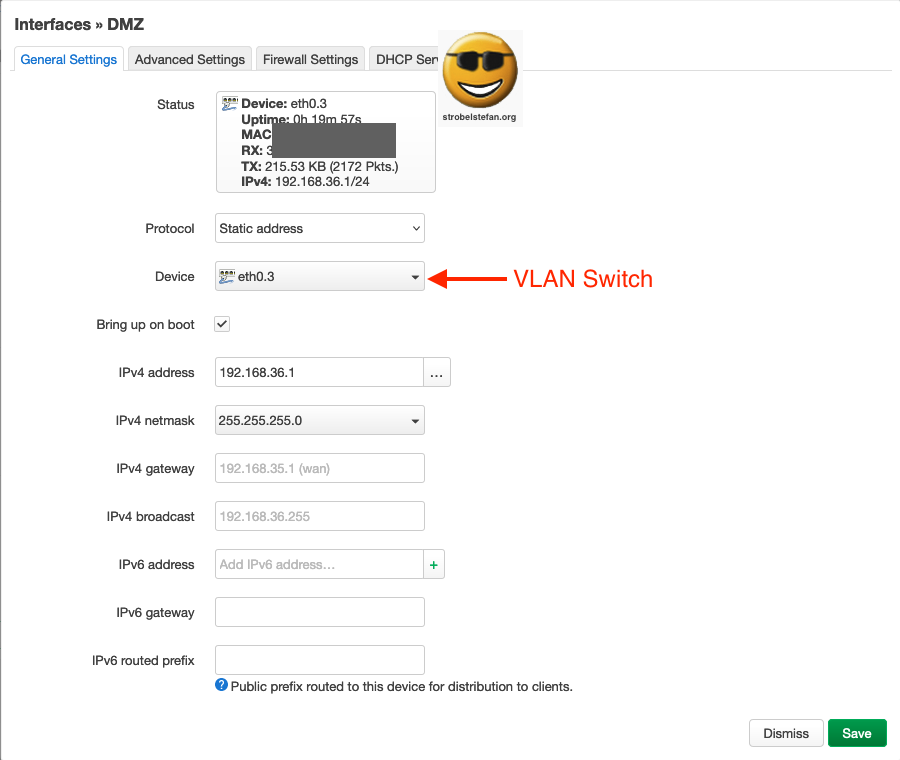
The Device should be the VLAN.
Advanced Settings
Firewall Settings
DHCP Server - General Settings
DHCP Server - Advanced Settings
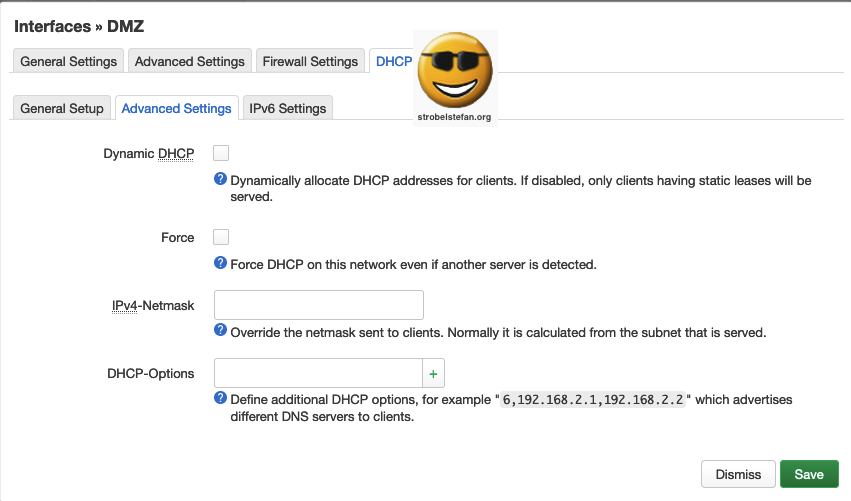
IPv6 Settings
Wireguard Interface
Please refer to the detailed WireGuard descriptions:
Wireless
The two wireless interfaces are deactivated.
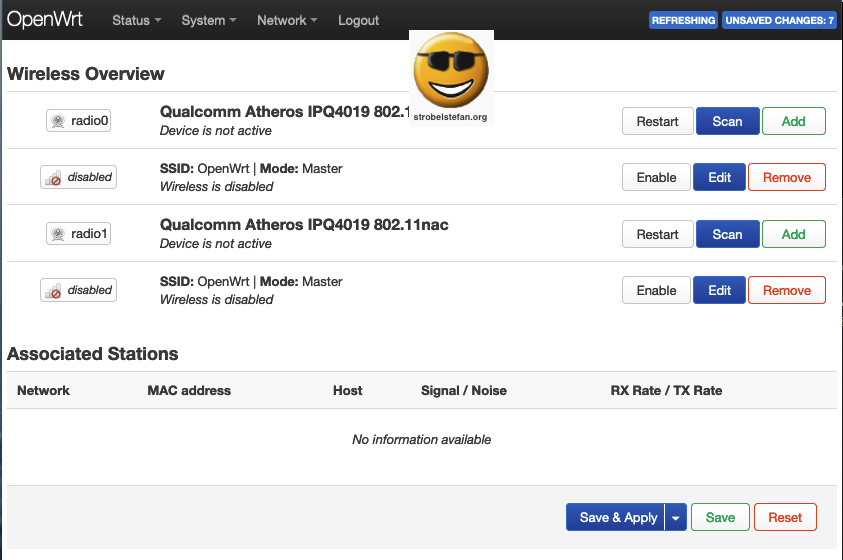
Switches
Standard switch configuration of OpenWrt after a fresh OpenWrt installation.
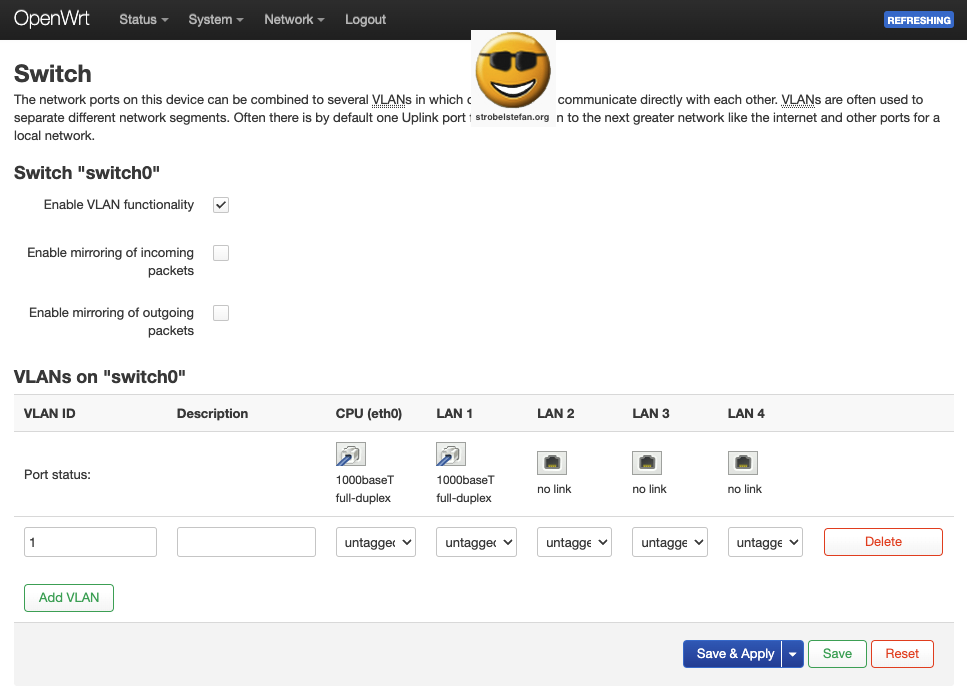
A new VLAN is created to make all devices plugged in to LAN 3 of AVM FRITZ!Box 4040 accessible from the internet, in this example a Nextcloud server.
It is important that the CPU port (= WAN port of the AVM FRITZ!Box 4040) is set to tagged. The port to which the device is connected (eth3 in this example) is set to untagged.
Menu: Netzwerk -> Switch
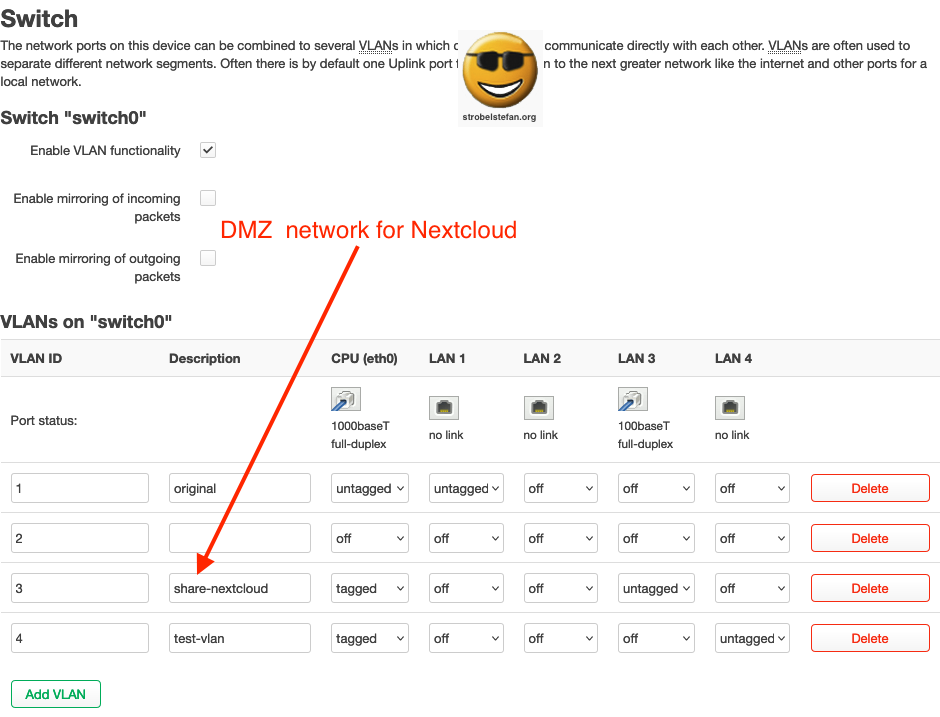
- CPU needs to be set to
tagged - LAN connection needs to be set to
untagged. This is the ethernet port where the device / network is plugged in.
🇬🇧 The purpose of a tagged port is to pass traffic for multiple VLANs, whereas an untagged port accepts traffic for only a single VLAN. Generally speaking, tagged ports will link switches, and untagged ports will link to end devices.
🇩🇪 Der Zweck eines getaggten Ports ist es, Datenverkehr für mehrere VLANs durchzulassen, während ein nicht getaggter Port nur Datenverkehr für ein einziges VLAN akzeptiert. Im Allgemeinen verbinden getaggte Ports Switches und nicht getaggte Ports Endgeräte.
Routing
Static IPv4 Routes
Static IPv6 Routes
Static IPv4 Rules
Static IPv6 Rules
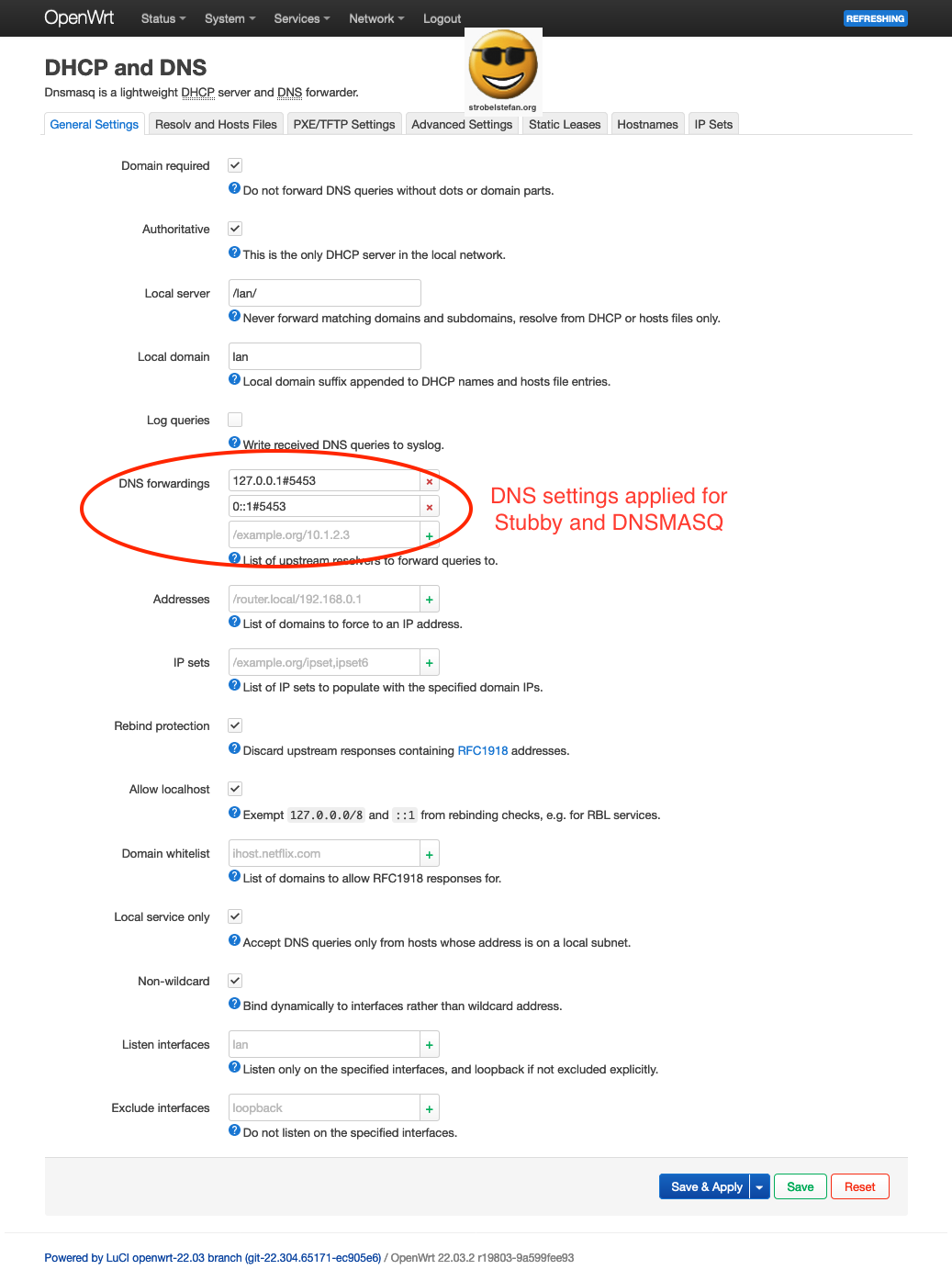
DHCP and DNS
The DNS settings are configured for Stubby and DNSMAQS ➡️ OpenWrt - Stubby & DNSMASQ
If you don't have Stubby DNSMAQS installed on your OpenWrt device, keep the default settings.
General Settings
Resolv and Host Files
PXE/TFTP Settings
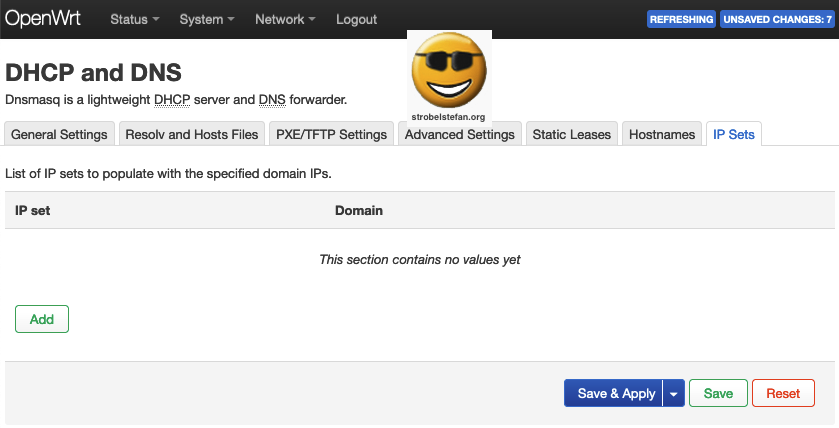
Advanced Settings
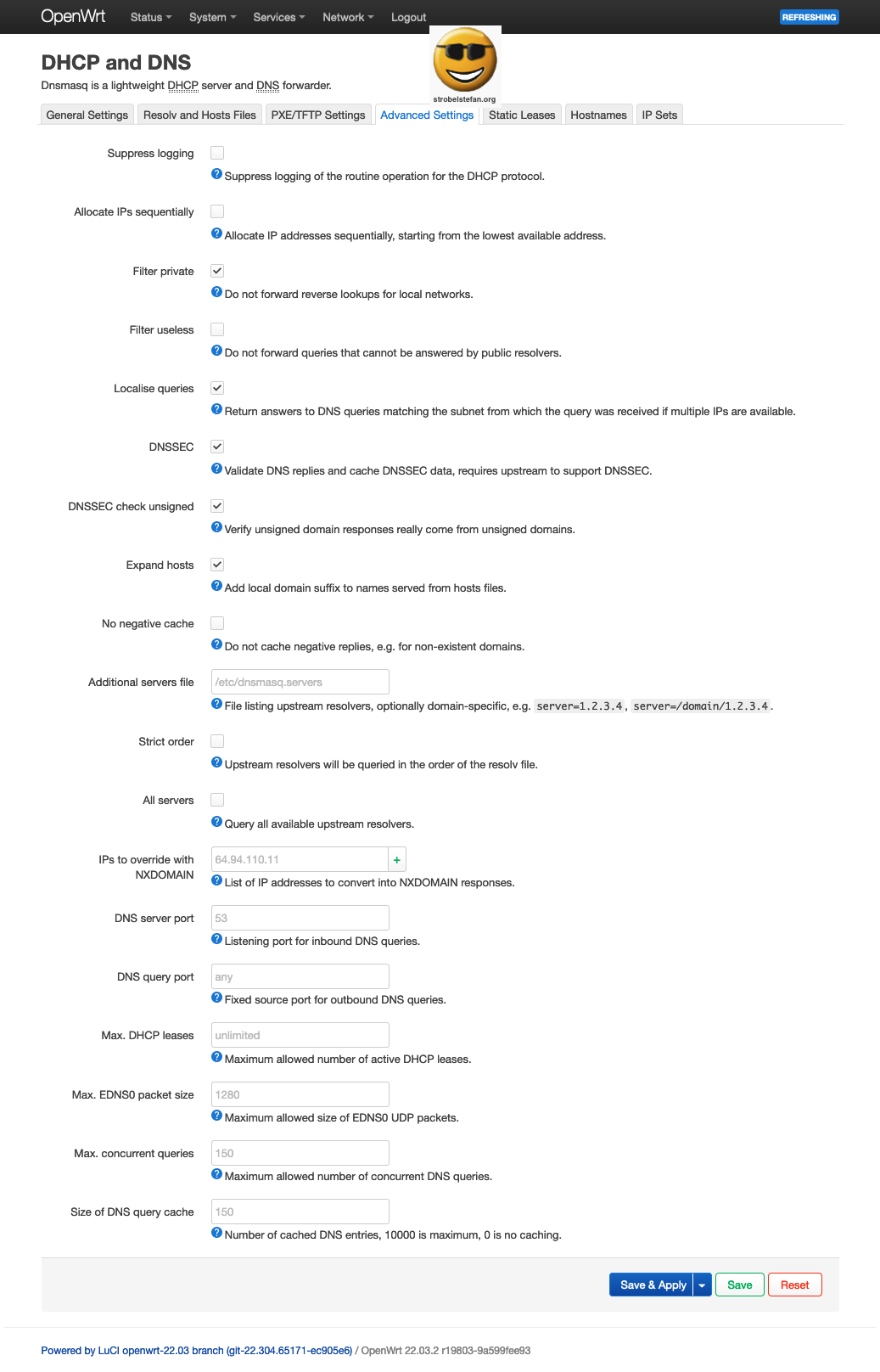
Static Leases
Hostnames
IP Sets
Firewall - General Settings
The OpenWrt setup uses the Firewall Zones as shown in the screenshot.
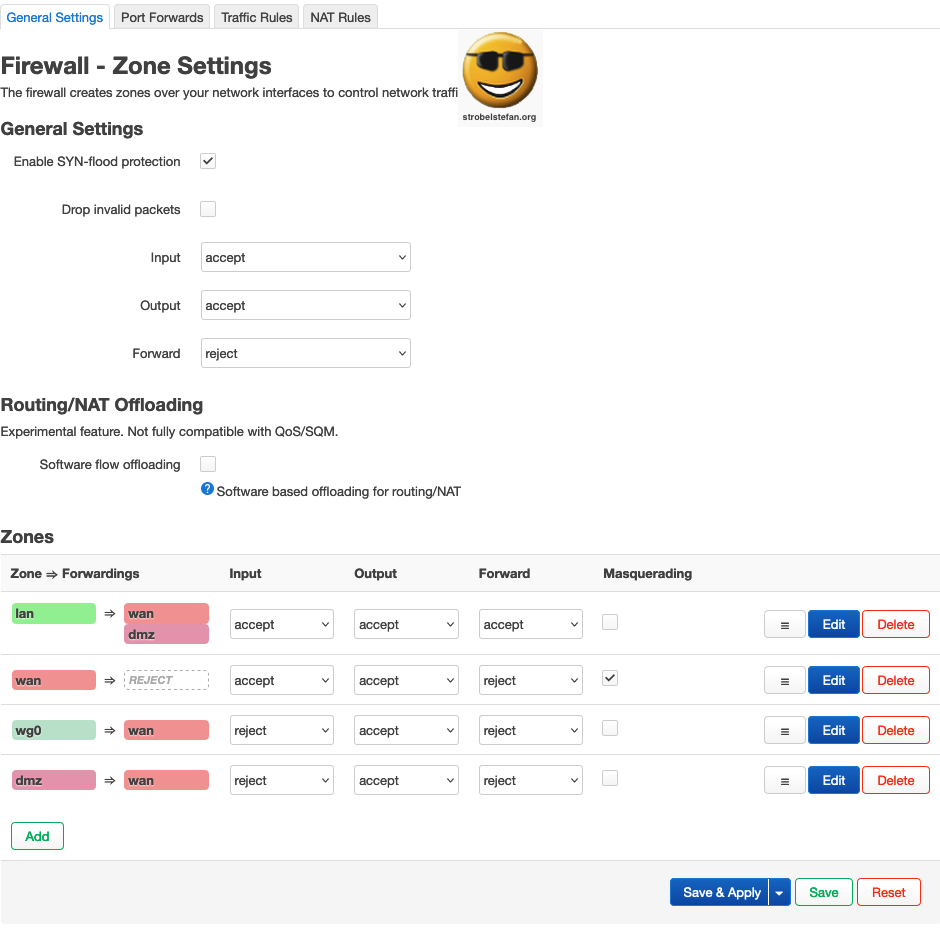
Firewall - Zone wan
⚠️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️
When input is set to reject it is not possible to access OpenWrt from wan!!!
⚠️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️ 🌩️
General Settings
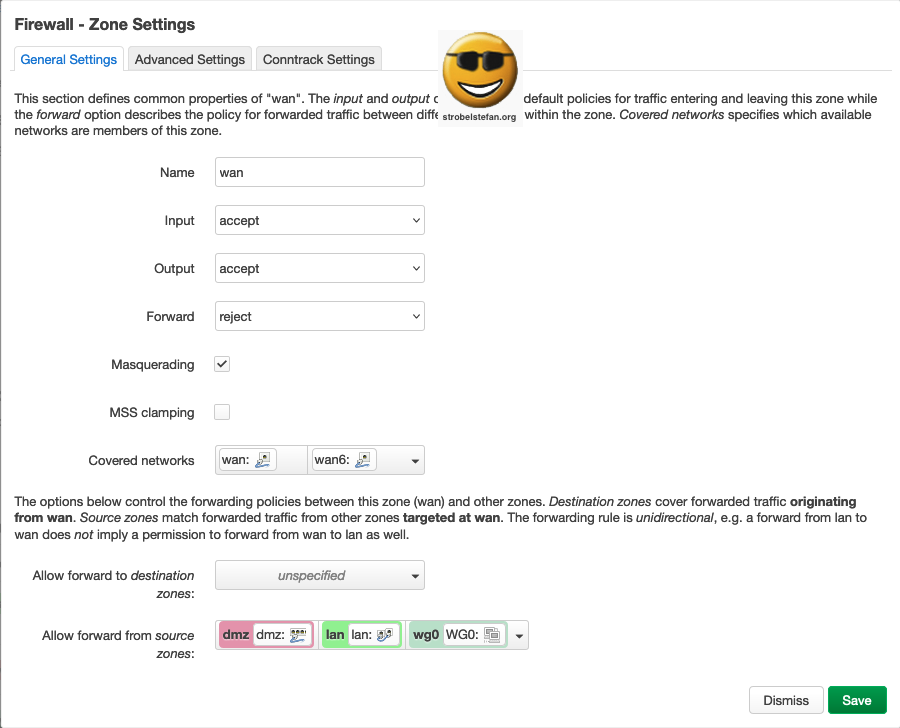
Advanced Settings
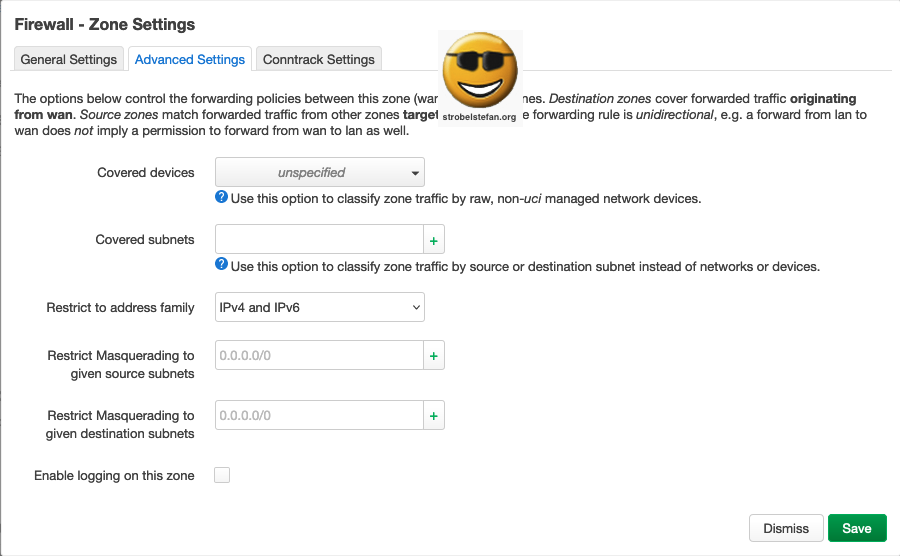
Conntrack Settings
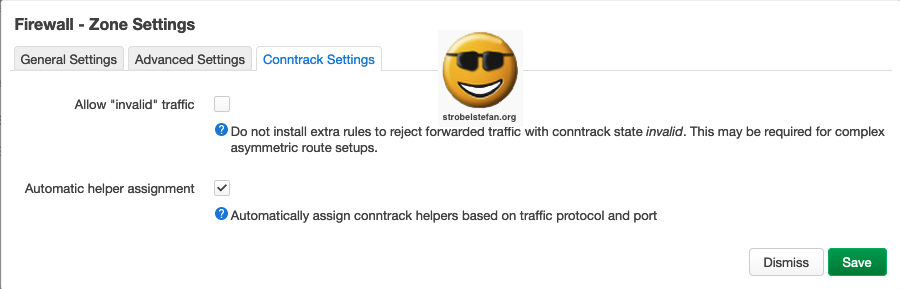
Firewall - Zone lan
General Settings
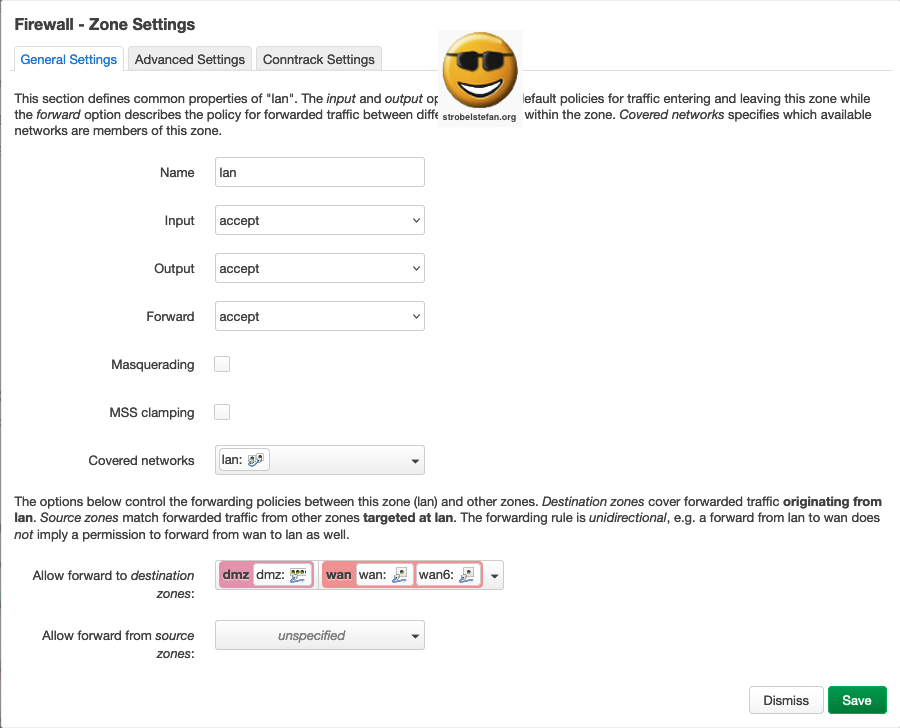
Advanced Settings
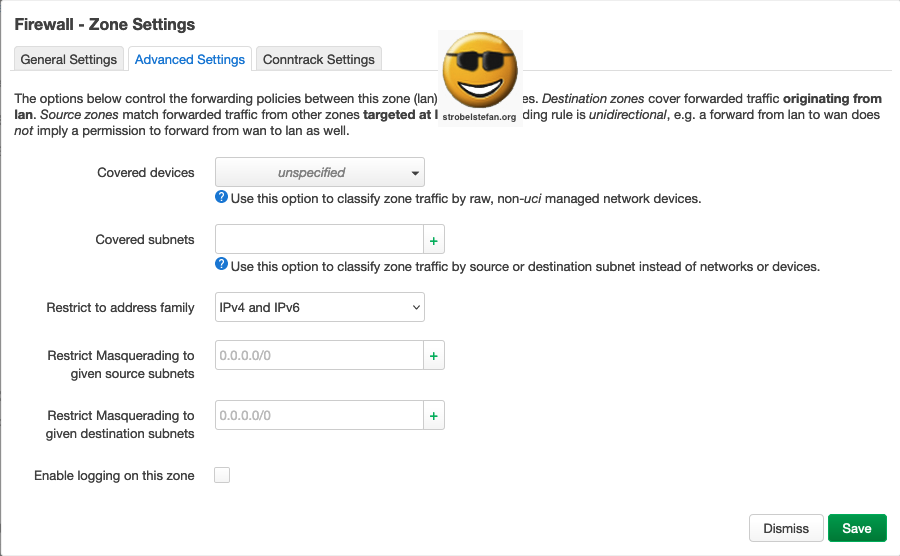
Comtrack Settings
Firewall - Zone dmz
General Settings
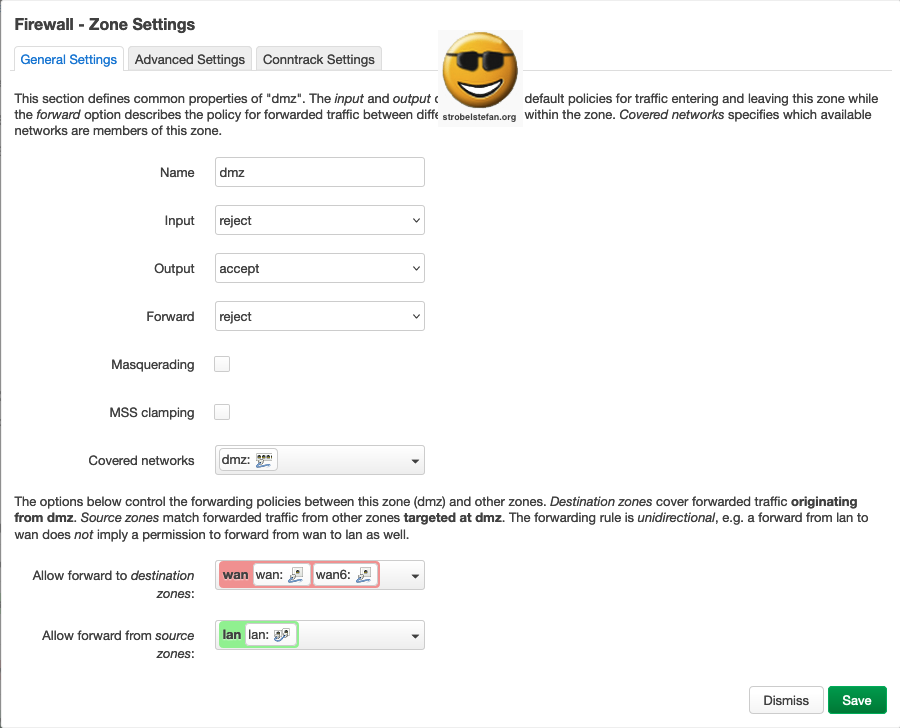
Advanced Settings
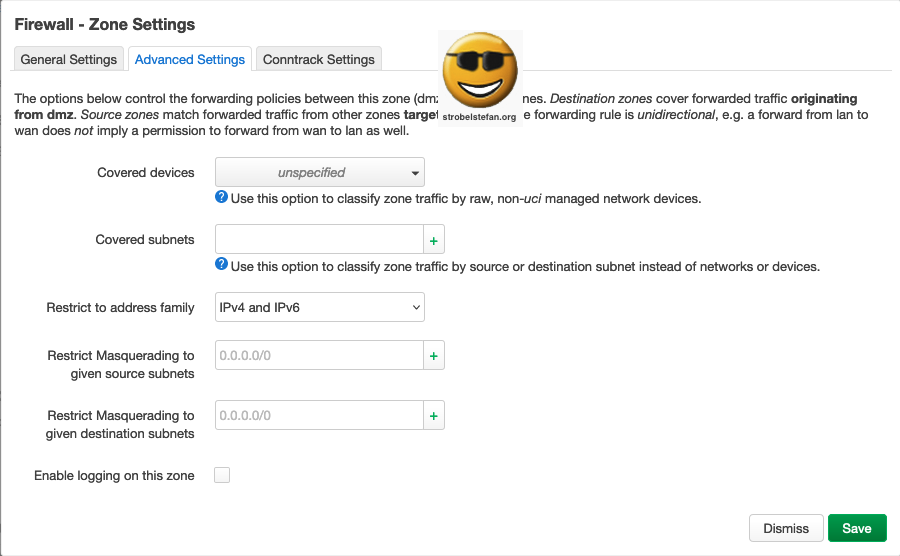
Conntrack Settings
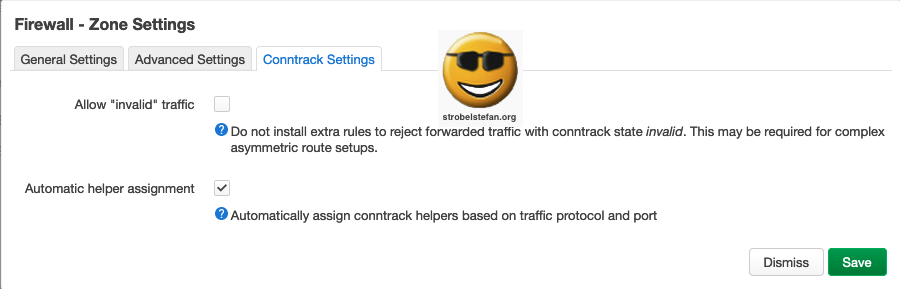
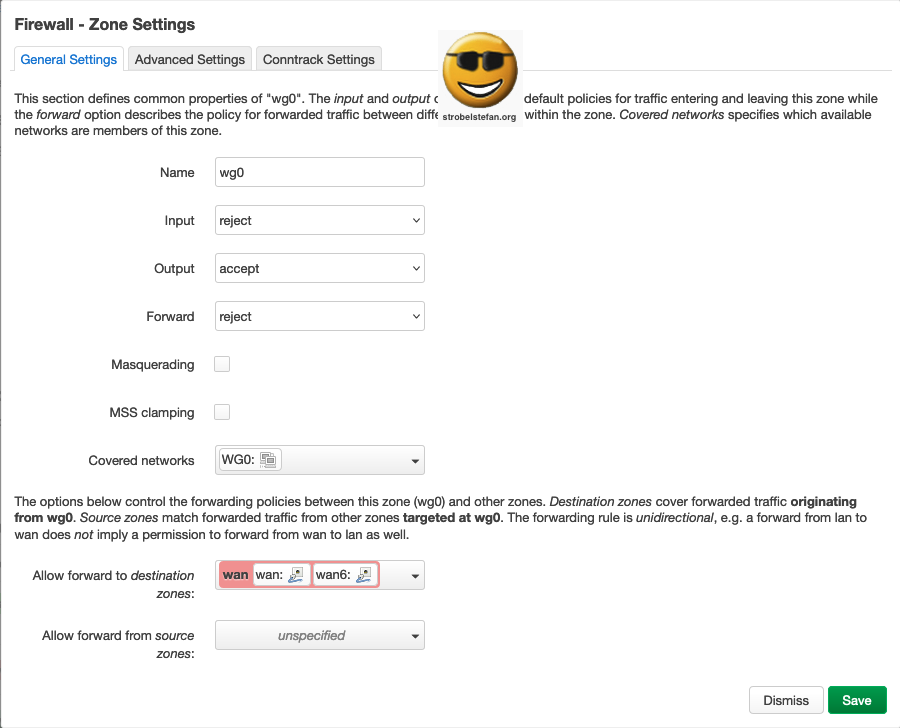
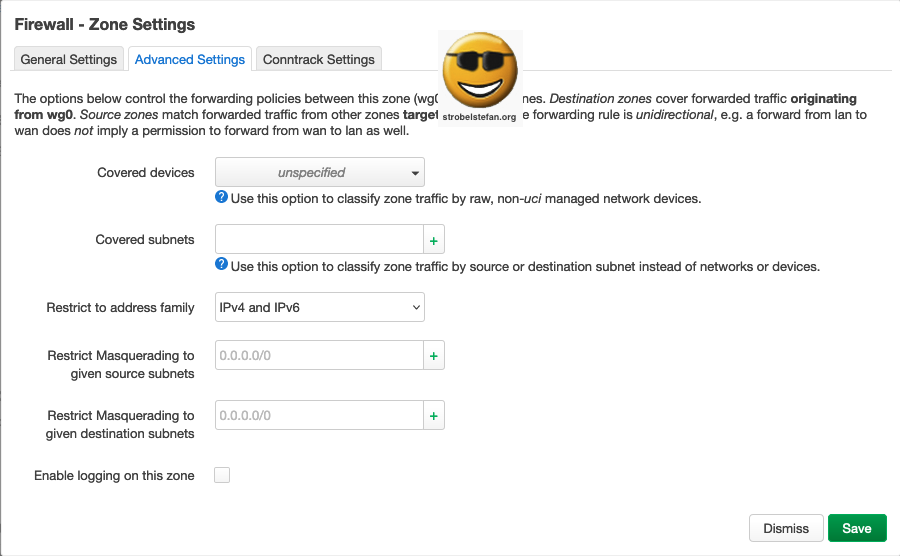
Firewall - Zone wg
Interface for the WireGuard VPN.
General Settings
Advanced Settings
Conntrack Settings
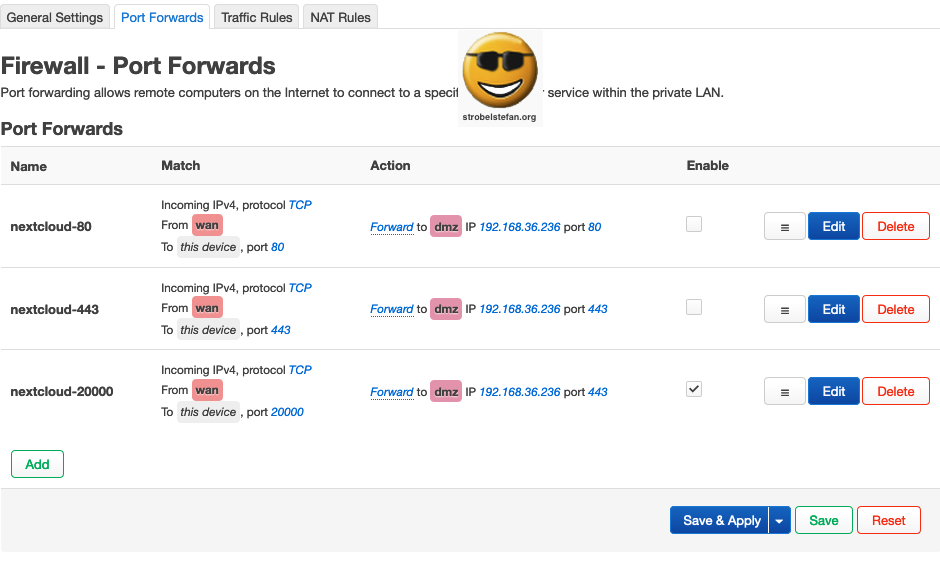
Firewall - Port Forwards
Port forwards are necessary that the device in the DMZ os accessible via defined ports from WAN. (The device is accessible from the internet. Please make sure that the respective ports are open on the router (= AVM FRITZ!Box 7490). ➡️ Portfreigaben
Port Forwards
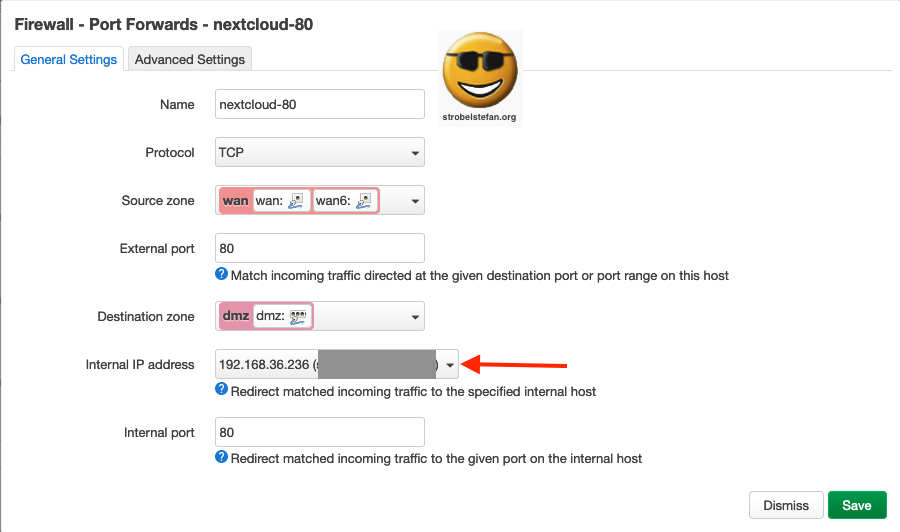
Firewall - Port Forwards nextcloud-80
This rule is only required for the renewal of Let's Encrypt certificate.
Port Forwards 80 - General Settings
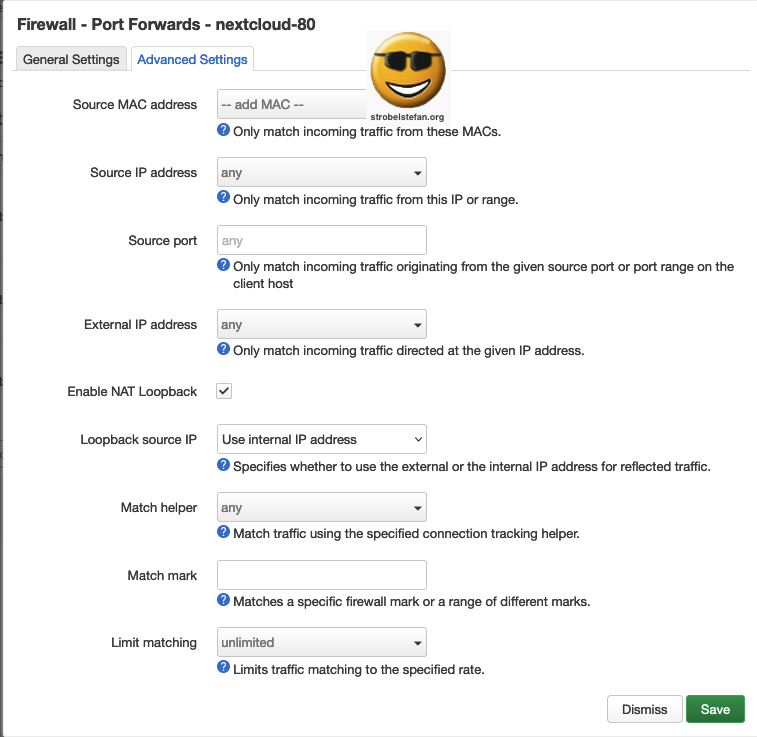
Port Forwards 80 - Advanced Settings
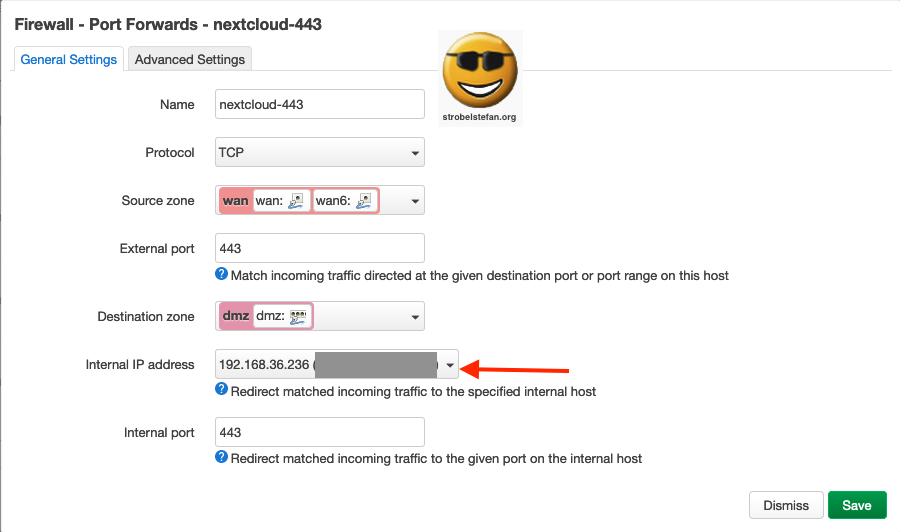
Firewall - Port Forwards nextcloud-443
This rule is only required for the renewal of Let's Encrypt certificate.
Port Forwards 443 - General Settings
Port Forwards 443 - Advanced Settings
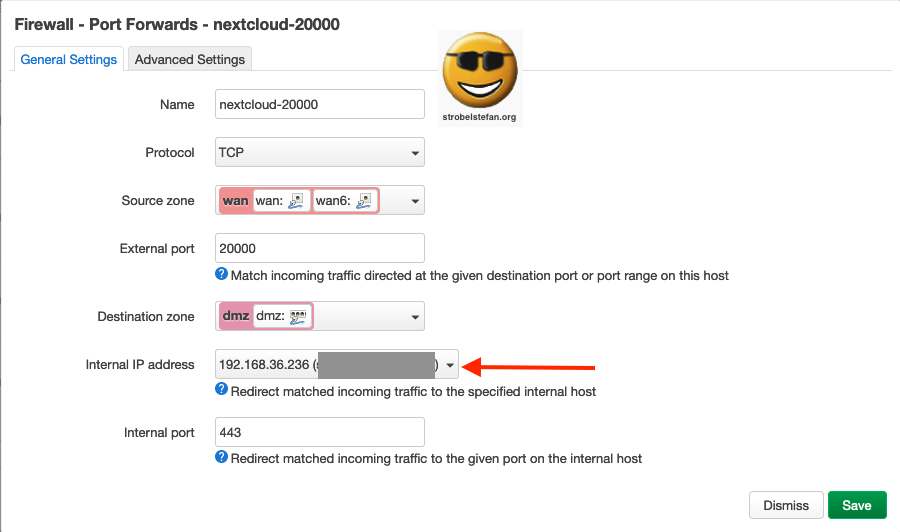
Firewall - Port Forwards nextcloud-20000
This rule makes the share.domain.de device accessible from the internet via port 20.000. When this rule is deactivated the Nextcloud won't be visible in the internet.
General Settings
Advanced Settings
More Port Forward Rules are configured for DNS. Please refer to ➡️ Hijack DNS for a detailed description.
Firewall - Traffic Rules
The traffic rules are hierarchically organized. The firewall goes from top to bottom. If it finds a match it stops regardless of the successive rules. The following rule will be ignored.
Traffic Rules - Overview
The screenshots show is an example. It shows not all rules described in this section.
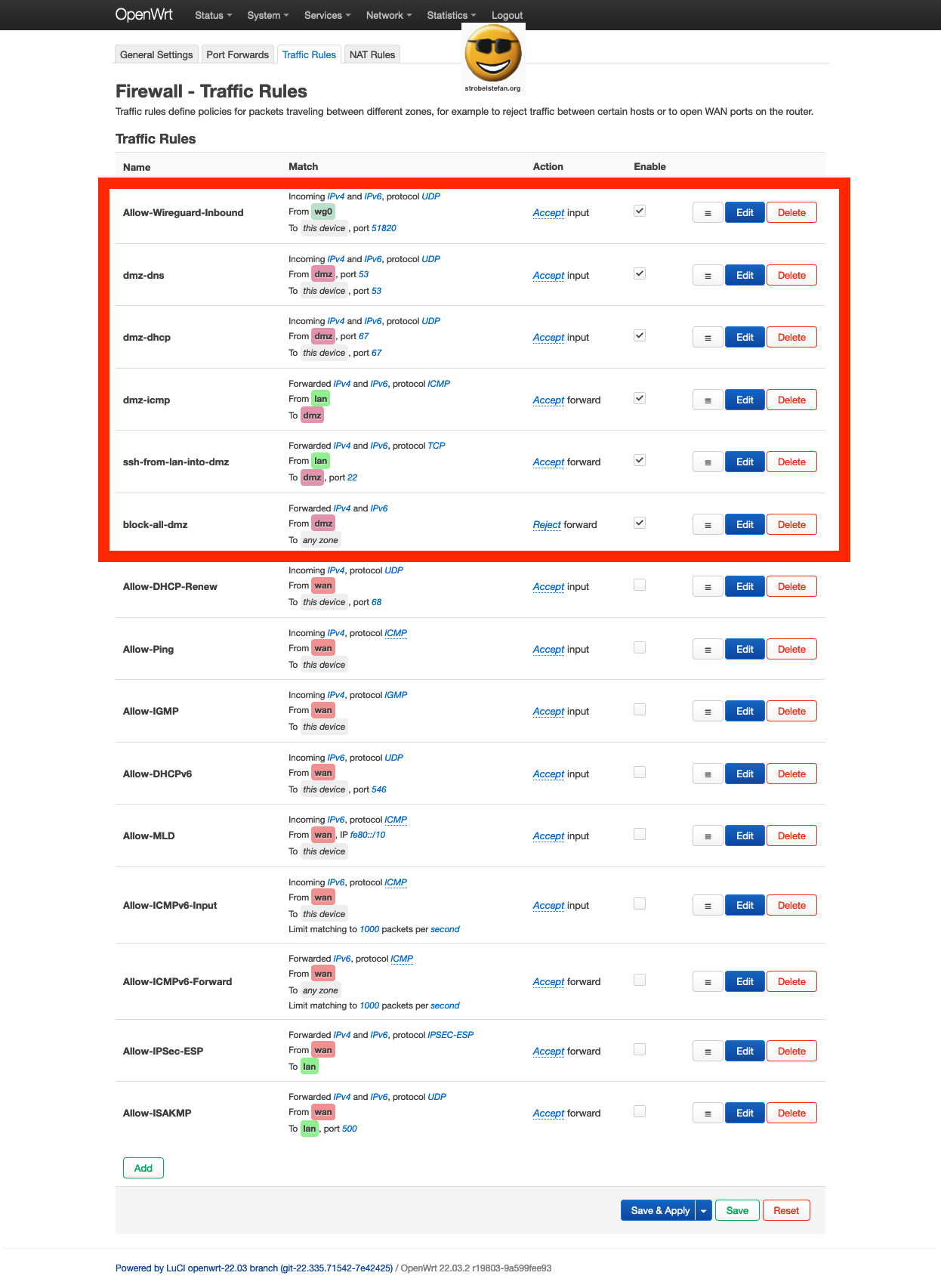
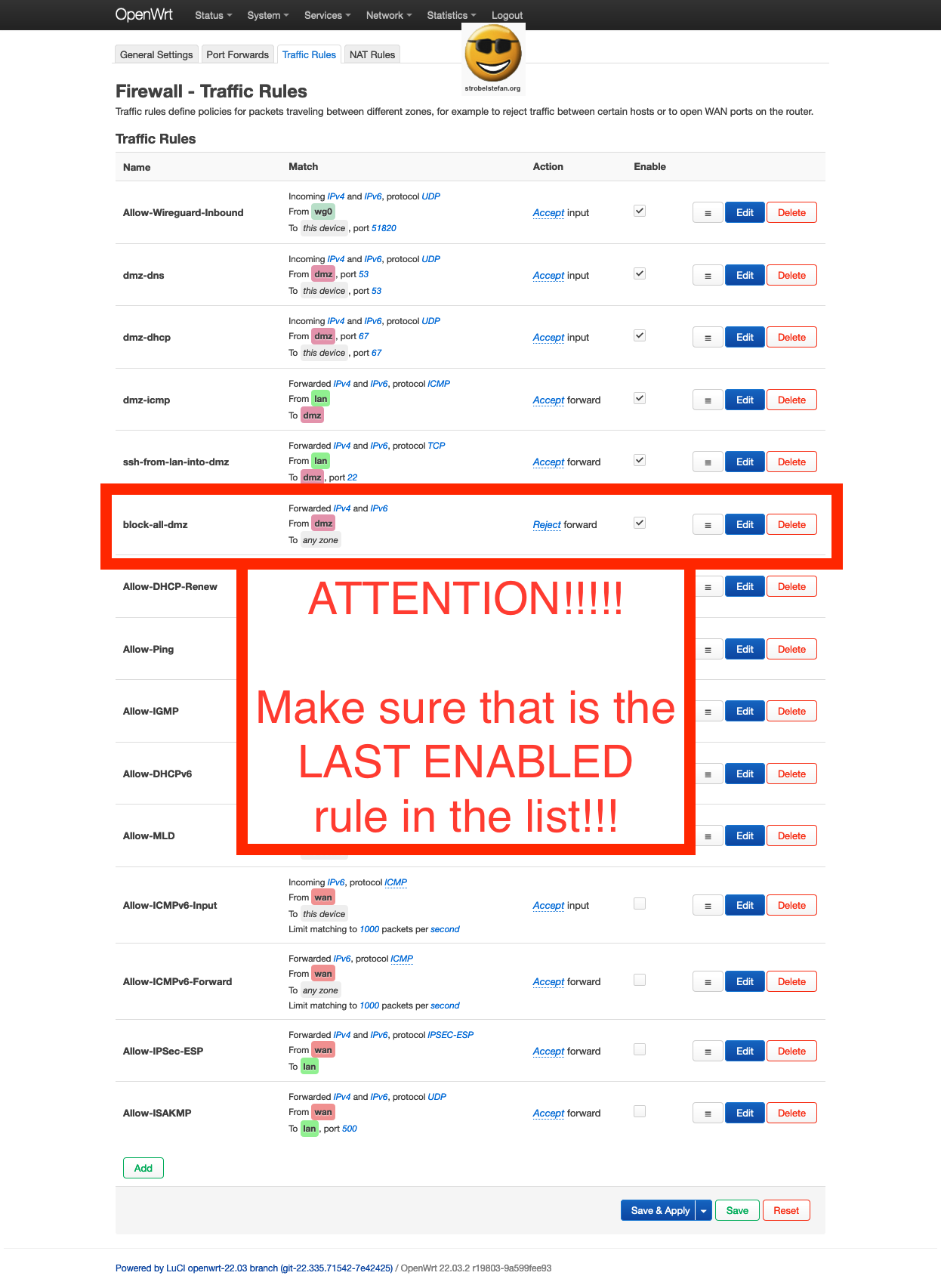
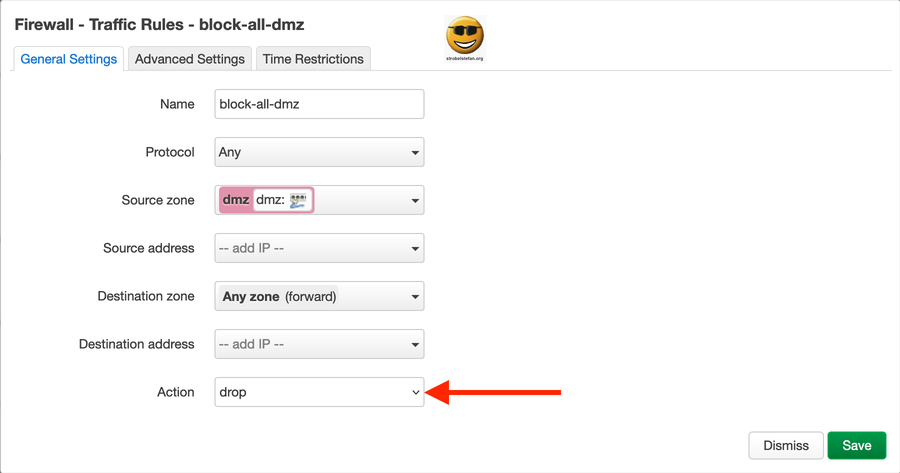
This block-all-dmz rule shall be the last active rule in your list. If you define new rules place them above this rule.
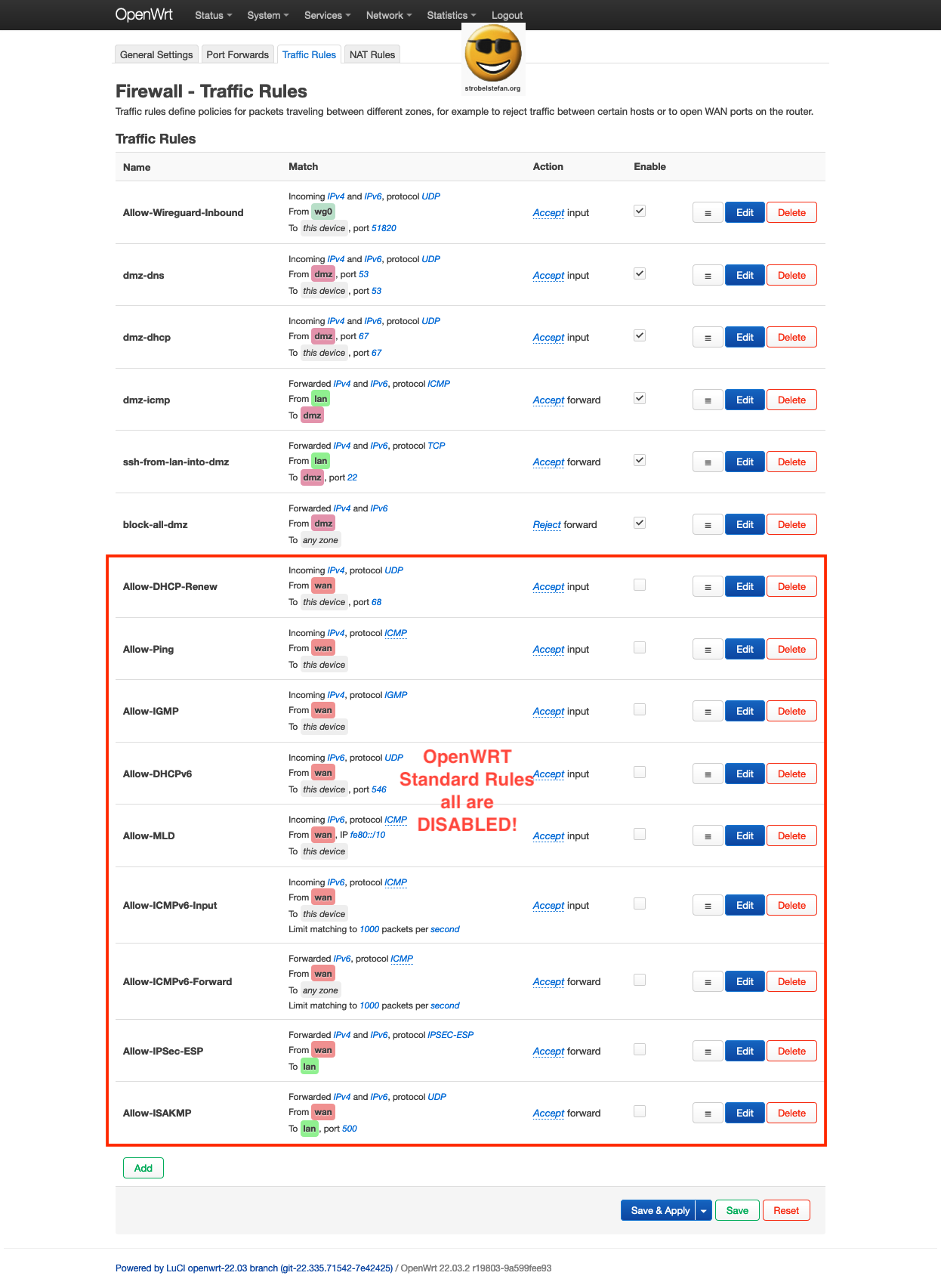
At the bottom all OpenWrt standard rules are listed. The rules are DISABLED.
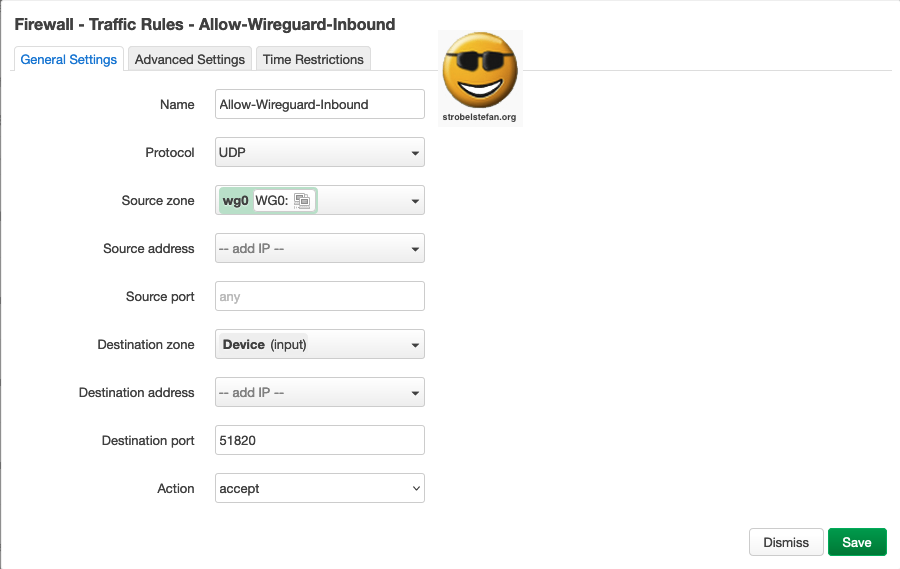
Firewall - Traffic Rules - Allow-Wireguard-Inbound
Allow-Wireguard-Inbound - General Settings
Allow-Wireguard-Inbound - Advanced Settings
Allow-Wireguard-Inbound - Time Restrictions
Firewall - Traffic Rules - dmz-dhcp
Traffic Rules - dmz-dhcp - General Settings
Traffic Rules - dmz-dhcp - Advanced Settings
Traffic Rules - dmz-dhcp - Time Restrictions
Firewall - Traffic Rules - dmz-dns-53
Traffic Rules - dmz-dns-53 - General Settings
Traffic Rules - dmz-dns-53 - Advanced Settings
Traffic Rules - dmz-dns-53 - Time Restrictions
Firewall - Traffic Rules - dmz-dns-853
Traffic Rules - dmz-dns-53 - General Settings
Traffic Rules - dmz-dns-853 - Advanced Settings
Traffic Rules - dmz-dns-853 - Time Restrictions
Firewall - Traffic Rules - dmz-allow-smtp
Traffic Rules - dmz-allow-smtp - General Settings
Traffic Rules - dmz-allow-smtp - - Advanced Settings
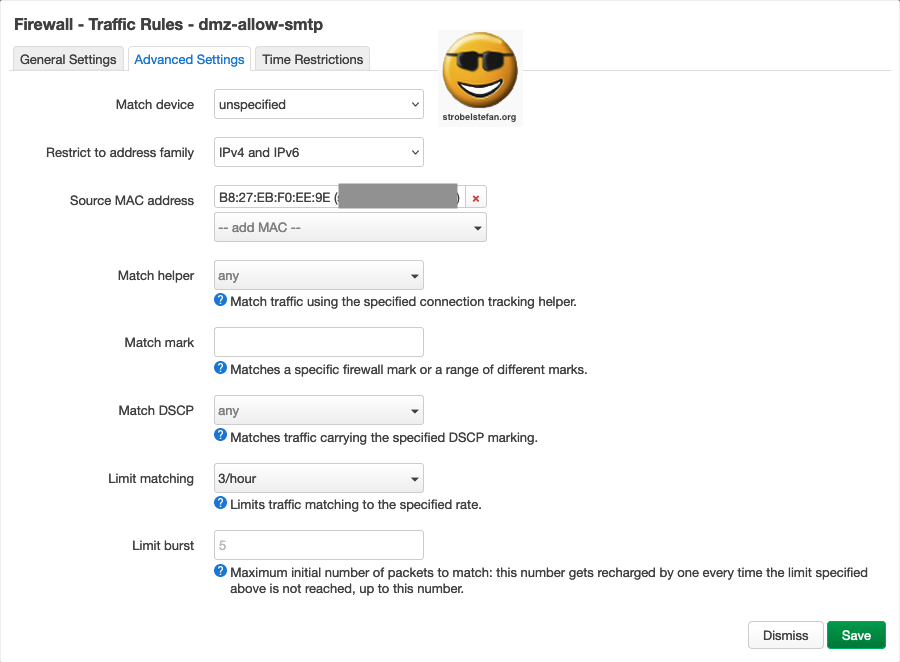
Traffic Rules - dmz-allow-smtp - Time Restriction
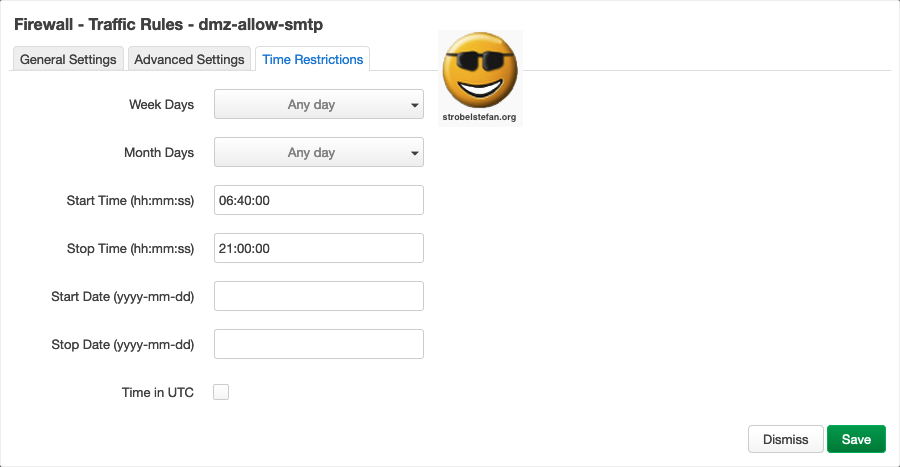
Firewall - Traffic Rules - dmz-http-https
This rule allows the Nextcloud server which runs on a Raspberry Pi to communicate with the repositories to update / upgrade installed software packages.
Without this rule the Raspberry Pi isn't able to ter the current lists.
Traffic Rules - dmz-http-https - General Settings
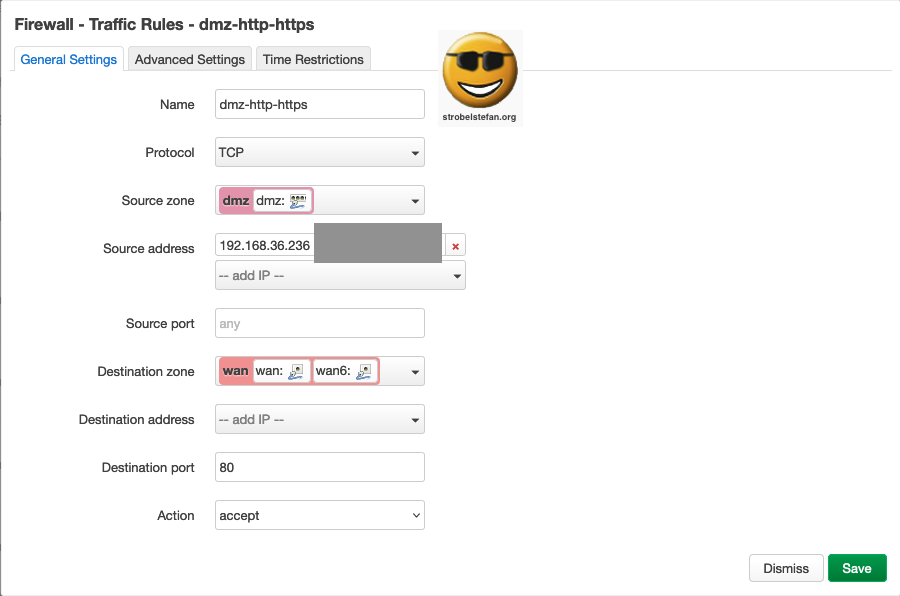
Traffic Rules - dmz-http-https - Advanced Settings
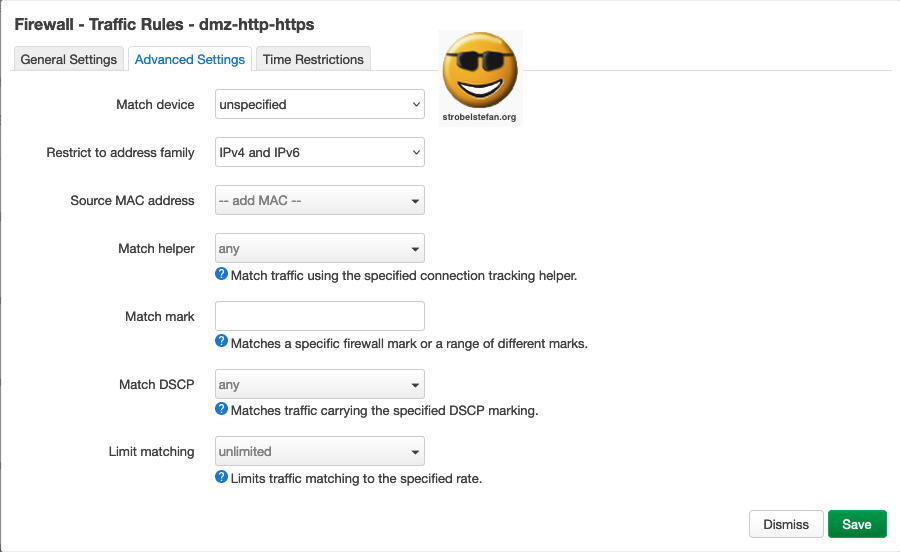
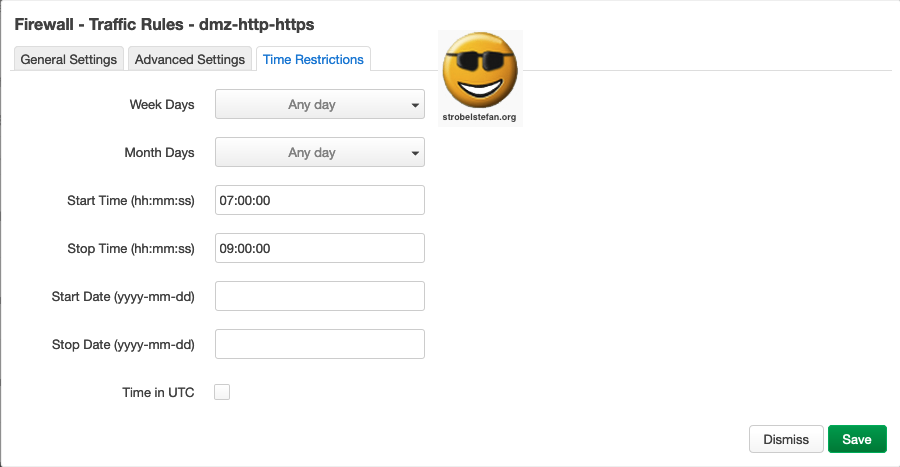
Traffic Rules - dmz-http-https - Time Restriction
The rule is time restricted! The devices in dmz can only access the wan is the specified time slot.
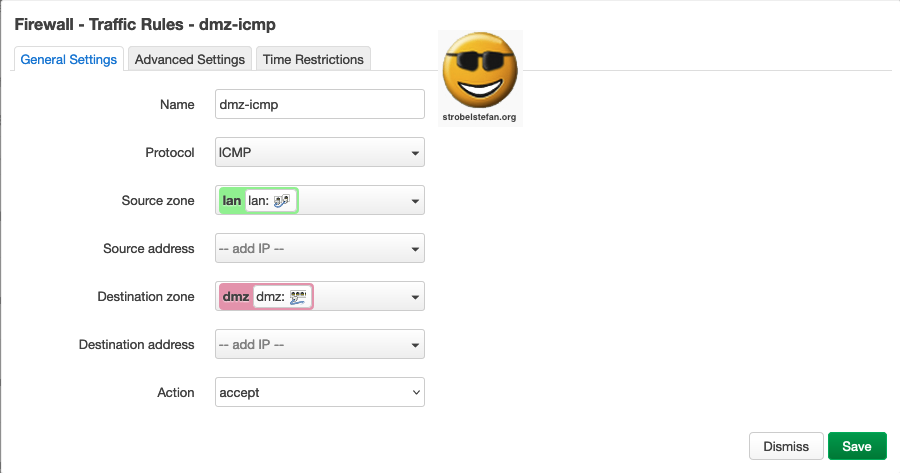
Firewall - Traffic Rules - dmz-icmp
Traffic Rules - dmz-icmp - General Settings
Traffic Rules - dmz-icmp - Advanced Settings
Traffic Rules - dmz-icmp - Time Restrictions
Firewall - Traffic Rules - ssh-from-lan-into-dmz
Traffic Rules - ssh-from-lan-into-dmz - General Settings
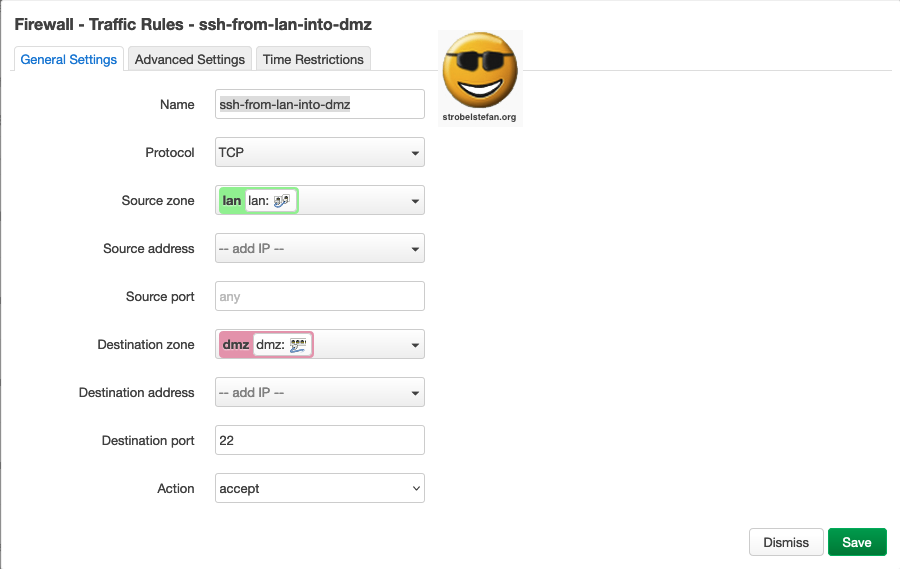
Traffic Rules - ssh-from-lan-into-dmz - Advanced Settings
Traffic Rules - ssh-from-lan-into-dmz - Time Restrictions
Firewall - Traffic Rules - block-all-dmz
This is n important rule. It will block all traffic which is not explicitly allowed to pass from dmz to any other network.
Traffic Rules - block-all-dmz - General Settings
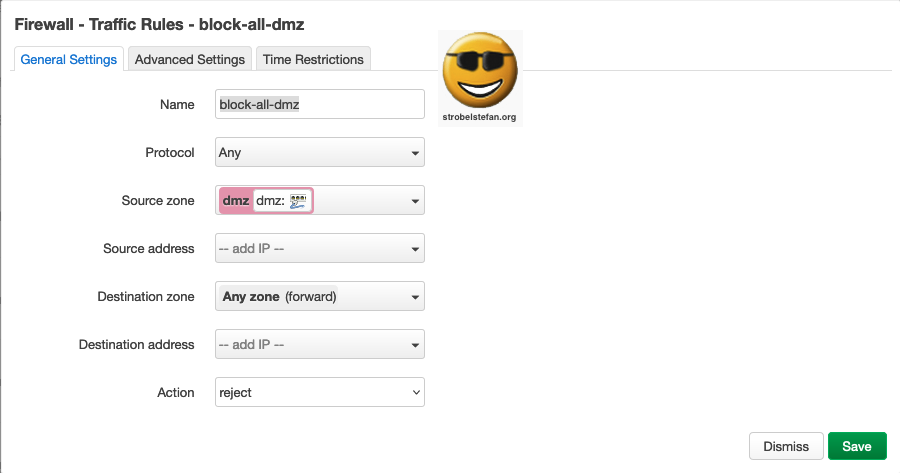
Traffic Rules - block-all-dmz - General Settings
Traffic Rules - block-all-dmz - General Settings
Firewall - NAT Rules
All articles of the OpenWrt series
Gib mir gerne einen Kaffee ☕ aus ❗️
Wenn dir meine Beiträge gefallen und geholfen haben, dann kannst du mir gerne einen Kaffee ☕️ ausgeben.
Follow Me❗️
Source
Official OpenWrt Logo - https://OpenWrt.org/_media/docs/guide-graphic-designer/OpenWrt-logo-usage-guidelines.pdf



